Politics
Commercial innovations to drive FedRAMP’s new approach

Now more than ever, the cloud security program known as FedRAMP needs industry’s help.
That was the message Monday from Pete Waterman, the director of the Federal Risk Authorization Management Program at the General Services Administration.
“We’re going to transform FedRAMP: Instead of the government deciding what is best, we’ll collaborate with industry to drive the solution. We’ll start now and update our approach continuously. We’ve all been talking about automating the status quo for way too long. Everyone in this room knows that if it was that easy, we would have done it by now,” Waterman said at an event sponsored by the Alliance for Digital Innovation on March 24. “We need to drive this type of change together as a community. You bring the solutions, we’ll vet them with agencies and set standards to match.”
Pete Waterman, the director of FedRAMP, speaks at the Alliance for Digital Innovation event. (Photo: Jason Miller/FNN)
Waterman said infrastructure-as-a-service and platform-as-a-service vendors can make their systems secure by design, or at least provide some capability so their customers using their services can validate their own security.
He said there are endless possibilities for third-party compliance tool vendors.
“Find your niche and build something cool. If you build validation software, you won’t be excluded anymore. We’ll all work with you to figure out multi-party validation in a way that includes you in the FedRAMP ecosystem without requiring a federal agency sponsor for everyone else,” Waterman said. “All the other cloud service providers of varying scale and complexity, you can adopt these capabilities, where, when and how. You can update your architecture to take advantage of them as they become available. Start small, go big and get secure. For everyone else, figure out where you can add value and plug in. There’s plenty of room inside this for new ideas.”
This new vision called FedRAMP 2025 is looking to industry for innovations and to help lead the effort is a drastic change from how GSA managed the program over the last 12 years.
Part of the reason for the new approach is the program management office is leaner with fewer contractor resources and a smaller budget. It also is getting out of being the centralized authority and provider of services, and will instead focus on setting policies and standards.
GSA and the Office of Management and Budget have tried repeatedly over the last decade to fix long-standing complaints and concerns about the program. The program management office and the Joint Authorization Board (JAB) created alternative approaches like FedRAMP Ready and FedRAMP Tailored, but the cost and burden of the authorization process still weighed heavily on agencies and vendors alike.
Waterman said says the new program management office will move on from the past of how GSA and OMB initially created the FedRAMP process.
“FedRAMP is rooted in the past. Federal Information Processing Standard (FIPS) 200, the government standard for the development, implementation and operation of secure information systems, was published way back in 2006. The approach outlined back then was based on the idea that systems were developed only until they were ready to be put into operation, like a building or a ship. You can use a paperwork based process to evaluate the security of something that you won’t change once it enters operation,” he said. “That hasn’t been how most of us built tech for a long time, though. Modern services are continuously and simultaneously developed and implemented while being operated without downtime and without stopping.”
Continuous validation is the goal
A common complaint about the current process is it’s too burdensome and costly, and it’s more of a checklist than a true security audit.
Instead, FedRAMP will work with industry to create continuous validation and verification processes as well as apply automation to those security controls.
“FedRAMP will set the standards that enable private innovation to create the solution. That’s how we’ll develop and continuously improve a standardized, reusable, cloud native approach to security assessment and authorization for cloud services,” he said. “We’re going to build a different approach, starting with understanding the underlying security principles that will ensure government information is safe in a continuously evolving commercial environment with key security indicators. Then together, we’ll build an assessment process to validate your choices about those key security indicators.”
While Waterman didn’t promise to have every answer to every question about how this new approach would work, there are some initial ideas that seem to make sense.
For example, the key security indicators would shift the requirements from extensive descriptions about each individual control on a spreadsheet to continuous validation that the intent behind those controls has been addressed and there would be no need for extensive human reviews.
“We know the capability to rely on automated validation for many security controls already exists and that host providers often offer secure by design options to make this easier for their customers,” Waterman said. “The vast majority of underlying security requirements for the NIST SP 800-53 can be validated in the same automated way if we approach them in the abstract. No one should ever be manually reviewing an old spreadsheet that has some screenshots next to it and pretend that that’s a security assessment.”
Waterman added he believes the ultimate goal of automating everything is effectively a Boolean decision.
- Can I trust this company? True or false
- Is this cloud service secure enough for my specific needs? True or false
- Will I authorize its use? True or false
“It’s that simple and that complex, but this should be our goal,” he said. “My team has already done a lot of work on this over the past couple of weeks to get started. Then you all tell me how you can help such offerings to validate their configuration. You don’t all have to agree on the approach or do it the same way. It’s the outcome that matters. If the approach is reasonable and the outcome is legit, we’ll validate the approach, any approach. From there, we just keep going, continually adding key security indicators and pulling in various existing frameworks as we simplify more and more controls and solve more complex use cases like multi-party, multi-service, multi-cloud validation eventually will come for the big IaaS and PaaS providers too. It won’t be as easy for you, but we’ll see it through, if you will. You can’t keep pushing paper forever. I don’t have all the answers to how to do this, but I’ll bring the coffee and donuts.”
Waterman will bring the proverbial coffee and donuts to four new community working groups FedRAMP is setting up to bring everyone together.
The PMO will hold the first meeting of the:
- The NIST SP-800-53, Rev 5 continuous monitoring working group on March 31
- The Automating assessment on April 2
- The applying existing frameworks group on April 8
- The continuous reporting group on April 10
“We’re going to set the tone and host some discussion, but a lot will depend on you and what you bring,” Waterman said. “I do want to be very, very clear that those groups are not to advise us. Those groups are not to give us consensus advice. Those groups are an attempt to create and establish a community where we work together and talk about things in public with each other, so there’s no more ghost rules and regulations. There’s just everybody has equal and fair access to all the same information, including me and my team, because my team wants to know what you all are doing. Then, as we monitor that, as we see things that work, and as we see some generally good ideas, and as we see standards that folks align towards, we will develop that standard that supports that, and then we’ll send that through our formal request for comment process that is required by law to make sure that we standardize that.”
Waterman said the PMO will use a GitHub discussion forum to post meeting notes and summarize the discussions and the progress of industry in addressing these challenges.
The post Commercial innovations to drive FedRAMP’s new approach first appeared on Federal News Network.
Politics
Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle

Screencap of YouTube video.
A Black Lives Matter activist in Boston named Monica Cannon-Grant pleaded guilty to federal charges this week, admitting that she scammed donors and used their money to fund her own lavish lifestyle.
Cannon-Grant was previously held up as an admired figure. The city of Boston named her the Bostonian of the year at one point for her ‘social justice activism’ and she was even recognized by the Boston Celtics basketball team for her efforts.
She is now facing a minimum of two years in prison.
The New York Post reports:
BLM-linked activist admits conning donors to fund her lavish lifestyle
A once-celebrated Boston social activist has pleaded guilty to defrauding donors — including Black Lives Matter — out of thousands of dollars that she used as a personal piggy bank.
Monica Cannon-Grant, 44, pleaded guilty Monday to 18 counts of fraud-related crimes that she committed with her late husband while operating their Violence in Boston (VIB) activists group, according to the US Attorney’s Office in Massachusetts.
The activist scammed money — including $3,000 from a BLM group — while claiming it was to help feed children and run protests like one in 2020 over the murder of George Floyd and police violence.
Cannon-Grant also conned her way into getting $100,000 in federal pandemic-related unemployment benefits — which she used to pay off her personal auto loan and car insurance policy.
But she has now confessed to transferring funds to personal bank accounts to pay for rent, shopping sprees, delivery meals, visits to a nail salon — and even a summer vacation to Maryland.
Just amazing.
Monica Cannon-Grant stole from donors, scammed the government, and lived it up while preaching about oppression. BLM grift is the only nonprofit where fraud is part of the mission statement. https://t.co/ir3q9lqYrh
— Matthew Newgarden (@a_newgarden) September 23, 2025
BREAKING: BLM activist Monica Cannon-Grant pleads guilty to 27 fraud charges, misusing over $1M from Violence in Boston for personal gain. Echoes Sir Maejor Page’s $450K scam conviction. A wake-up call for nonprofit accountability. pic.twitter.com/N9vvD369gB
— (@pr0ud_americans) September 14, 2025
Here’s a local video report:
She should pay back every penny.
The post Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle appeared first on The Gateway Pundit.
Politics
Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO)

As the Gateway Pundit reported yesterday, former MSNBC host and generally unhinged leftist Keith Olbermann, appeared to threaten CNN’s conservative pundit Scott Jennings on Twitter saying, ‘You’re next motherf**ker.’
Well, Olbermann may have gotten a phone call or a visit from the FBI because today he walked back those comments with a full-throated apology.
RedState has an update:
To quickly recap, Scott Jennings, a Salem Media Network radio host and conservative CNN political commentator, reacted to breaking news on Monday that Kimmel had been reinstated by tweeting, “So basically his employer suspended him for being an insensitive pr**k, and we don’t live in an authoritarian regime? Got it.”
This enraged Olbermann, who proceeded to tweet what many, including Jennings, perceived to be a threat. “You’re next, motherf**ker. But keep mugging to the camera.” Jennings tagged Patel and included a screengrab of the tweets in response.
Though the FBI hasn’t commented as to whether an investigation was launched, Olbermann ostensibly appears to have thought twice about what he tweeted and deleted, apologizing profusely in tweets posted on Tuesday and claiming what he wrote was “misinterpreted”:
See Olbermann’s tweet below:
I apologize without reservation to @ScottJenningsKY
Yesterday I wrote and immediately deleted 2 responses to him about Kimmel because they could be misinterpreted as a threat to anything besides his career. I immediately replaced them with ones specifying what I actually meant. pic.twitter.com/SPWLb73nEk
— Keith Olbermann (@KeithOlbermann) September 23, 2025
I oppose and condemn political violence, and the threat of it. All times are the wrong time to leave even an inadvertent impression of it – but this time is especially wrong
I should've acknowledged the deletion and apologized yesterday. I'm sorry I delayed.
— Keith Olbermann (@KeithOlbermann) September 23, 2025
Scott Jennings, always a class act, offered this hilarious response:
SCOTT JENNINGS: “Marking myself SAFE from that NUT, Keith Olbermann!” pic.twitter.com/EYZX6vm5Oh
— Dustin Grage (@GrageDustin) September 23, 2025
Keith Olbermann really needs help. The guy is just so out of control.
The post Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO) appeared first on The Gateway Pundit.
Politics
Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished

 Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson lived with his transgender partner – a male-to-female trans named Lance “Luna” Twiggs.
The FBI used Robinson’s texts with his transgender partner to solidify that Robinson was the assassin. Lance Twiggs has not been charged with any crime; however, federal authorities are still investigating.
Last week, Utah authorities released the text exchange between Tyler Robinson and his transgender lover, Lance Twiggs, sent shortly after Kirk’s assassination.
Utah County District Attorney Jeff Gray announced seven charges against Charlie Kirk assassin Tyler Robinson. They will also be seeking the death penalty.
Robinson was charged with:
– Count 1: Aggravated murder (capital offense)
– Count 2: Felony reckless discharge of a firearm causing bodily injury
– Count 3: Felony obstruction of justice for hiding the firearm
– Count 4: Felony obstruction of justice for discarding the clothing he wore during the shooting
– Count 5: Witness tampering for asking roommate to delete incriminating messages
– Count 6: Witness temperating for demanding trans roommate stay silent, and not speak to police
– Count 7: Commission of a violent offense in the presence of a child
Jeff Gray released the chilling texts between Tyler Robinson and his “love” Lance Twiggs.
Read the text exchange here:
 Tyler Robinson texts with transgender lover Lance Twiggs / 1
Tyler Robinson texts with transgender lover Lance Twiggs / 1
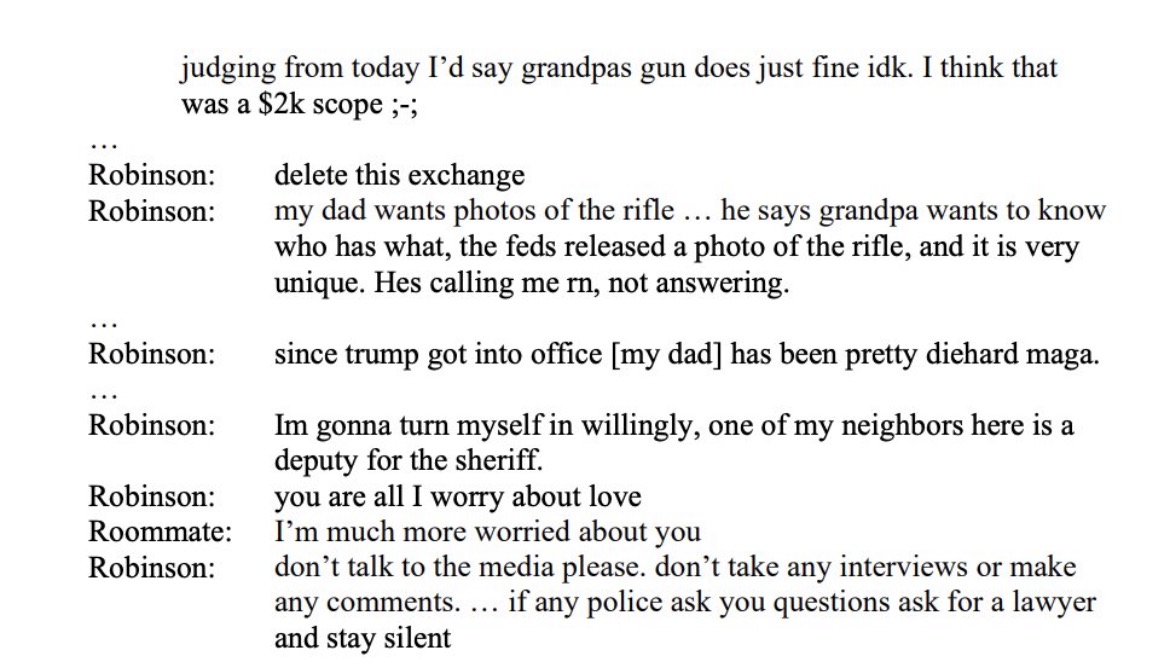 Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Lance Twiggs was reportedly cooperating with the FBI, however, according to the Daily Mail he has seemingly vanished.
“If [Lance Twiggs] ever comes back, it will be in a body bag,” a neighbor said to the Daily Mail. “That’s not a threat – I’m just saying that there are so many people who want a piece of him he’d be mad to show his face in public again. This was a generational event.”
The Daily Mail reported:
The Trans boyfriend of Charlie Kirk’s alleged assassin has fled their former lovenest – and locals tell the Daily Mail they never want to see him again.
Lance Twiggs, 22, was led away for questioning when police swooped on the smart three-bed condo he shared with accused gunman Tyler Robinson, 22.
Shaken neighbors say the part time plumber has not been back to the $320,000 property in St. George, Utah – one declaring: ‘Good riddance. I never want to see either of them again.’
His beaten-up Infinity compact is still parked in his space with his work gear tossed across the back seat and a sandwich wrapper and a drink on the front passenger seat.
Upstairs lights have been left on for more than a week and notes and Amazon packages are piling up outside the home owned by Twiggs’s devout Mormon family.
The post Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished appeared first on The Gateway Pundit.
-
 Entertainment6 months ago
Entertainment6 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment3 months ago
Entertainment3 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech6 months ago
The best sexting apps in 2025
-
 Entertainment5 months ago
Entertainment5 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech7 months ago
Tech7 months agoEvery potential TikTok buyer we know about
-
Tech7 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech7 months ago
Tech7 months agoAre You an RSSMasher?
-

 Politics7 months ago
Politics7 months agoDOGE-ing toward the best Department of Defense ever



