Politics
WATCH: CNBC’s Joe Kernan Humilates Hakeem Jeffries With a Few Inconvenient Facts After House Dem Leader Tries to Push His Lies Regarding Government Shutdown
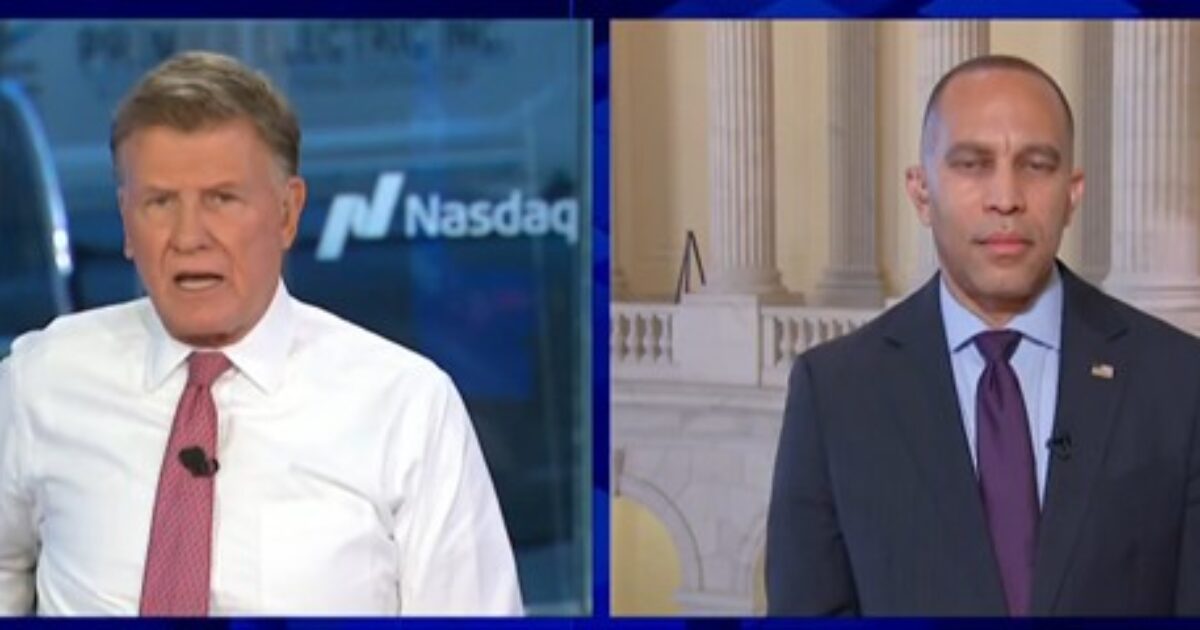
CNBC’s Joe Kernan hits House Minority Leader Hakeem Jeffries with brutal facts on Schumer shutdown, leaving Jeffries embarrassed. Credit: CNBC screenshot
House Minority Leader Hakeem Jeffries continues to embarrass himself in his efforts to convince Americans that Republicans are responsible for the government shutdown caused by him and his fellow Democrats.
As The Gateway Pundit reported, the Schumer Shutdown took effect at 12:01 am on October 1 after two measures to avert the government shutdown failed in the Senate.
The measures needed 60 votes to pass. The GOP-backed measure failed to pass in a 55-45 vote – Rand Paul voted with the Democrats.
The Democrat Party and Paul decided to put the welfare of illegal aliens, higher taxes by repealing Trump’s “Big, Beautiful Bill, surgeries for transgender minors, and more garbage ahead of keeping the government running.
Several more GOP votes have been held to reopen the government, but Democrats have remained firm in their obstinacy.
On Thursday, Squawk Box co-host Joe Kernan confronted Jeffries with a few brutal facts after the House Democratic leader recited his failed talking points. Kernan noted there was an election Republicans won, and because of that, they were to pass legislation such as Trump’s “Big, Beautiful Bill.”
Kernan noted that trying to reverse such legislation in a government funding bill was extraordinarily hypocritical because if the GOP tried to shut down the government under legislation passed under the Biden regime, Jeffries would be screaming.
The CNBC co-host then said this was not how government works and that the bill currently on the table has bipartisan support in the Senate.
Jeffries had no answer for this and could only whine about Republicans not engaging in bipartisan negotiations and that they could reopen the government at any time.
Of course, he neglected to say that it takes 60 votes in the Senate to pass a bill, should one side decide to filibuster. This is what Democrats are doing right now.
Kernan’s fellow co-host, Becky Quick, also told Jeffries that he could engage in bipartisan negotiations after the government reopens, noting the number of Republicans anxious to make a deal on the Obamacare subsidies.
This was certainly not precisely the interview Jeffries expected.
WATCH:
BREAKING: Hakeem Jeffries was just EMBARRASSED for holding the government hostage…holy smokes. This was bad.
CNBC: “There was an ELECTION. Republicans were able to pass the Big Beautiful Bill. To then say, ‘We don’t like that, so we’re gonna shut down the government until… pic.twitter.com/wlcxytaZC6
— Eric Daugherty (@EricLDaugh) October 9, 2025
KERNAN: There was an election, and the Republicans were put in a position where they were able to pass the Big Beautiful Bill.
To then say, ‘We don’t like that, so we’re gonna shut down the government until you take back all the things you duly passed through legislation…If the Republicans tried to do that to the Inflation Reduction Act, or any of the Biden acts, shut down the government because we don’t like it, not pay military, not allow the government to open until you do what we want, after an election when the American people put Democrats in power, you’d be going crazy.
You’d be going crazy about using a shutdown of the federal government on a continuing resolution to get what you want, cause you don’t like what Republicans did.
“It’s not how it works. It’s bad, it’s bad precedent…And you’re talking about the House? You’ve already passed this.
The Senate has a bill to reopen the government right now with five more Democrats.
JEFFRIES: What is bad precedent is the Republican refusal to engage in bipartisan negotiations. What is bad precendent is Republicnas embarking on a my way or the highway approach from the beginning of this Congress.
Republicans control the House, the Senate, and the Presidency…So if the government shuts down, they’ve made the government shutdown.
They could reopen it right now.
KERNAN: How could they do that?
JEFFRIES: I just explained it. They want to keep it closed.
Cruelty from the very beginning has been the point. The responsible thing to do is to sit down and negotiate a bipartisan path forward.
QUICK: Minority Leader, can you do that while the government is open? That’s the offer on the table.
House Speaker Mike Johnson passed a clean CR. There’s nothing to politick with because there’s nothing to take out.
You can reopen the government and have the conversations (on health care). It sounds like there is a willing party on the other side (Republicans) who see this as an issue in their district as well.
JEFFRIES: Marjorie Taylor Greene has made clear that this is an issue Republicans have ignored throughout this year, and it needs to be addressed right now.
The post WATCH: CNBC’s Joe Kernan Humilates Hakeem Jeffries With a Few Inconvenient Facts After House Dem Leader Tries to Push His Lies Regarding Government Shutdown appeared first on The Gateway Pundit.
Politics
NEW: FBI Fires Two Agents Who Worked For Jack Smith

The FBI took action against three FBI officials who worked for Jack Smith, firing two, after it was revealed that Biden’s FBI – and Jack Smith – spied on several Republican Senators.
According to NBC News, one of the fired FBI agents was months away from retirement.
Joe Biden’s FBI – and later Jack Smith – spied on eight Republican Senators during the ‘Arctic Frost’ investigation into January 6.
Republican Senators Chuck Grassley and Ron Johnson earlier this year released new records detailing the FBI and DOJ’s sweeping investigation that formed the basis of Jack Smith’s DC case against President Trump.
Grassley and Johnson previously blew the lid off another sham investigation orchestrated by Biden’s corrupt Department of Justice and compromised FBI.
According to the documents released earlier this year, the FBI and DOJ weaponized their power to target President Trump, former Vice President Mike Pence, and their allies through a probe dubbed “Arctic Frost.”
“Operation Arctic Frost” was a taxpayer-funded witch hunt launched in April 2022 that seized government-issued cell phones belonging to Trump and Pence while conducting a barrage of interviews across the country.
Jack Smith tracked private phone calls of eight GOP Senators.
Here’s the list:
 FBI, Jack Smith spied on Republican Senators and tracked their calls
FBI, Jack Smith spied on Republican Senators and tracked their calls
FBI Director Kash Patel previously said he fired those who ‘acted unethically’ but it was unclear how many agents he terminated.
They tracked the communications of GOP Senators. They weaponized law enforcement against the American people. That era is over.
We fired those who acted unethically, dismantled the corrupt CR-15 squad, and launched an investigation.
Transparency and accountability aren’t… pic.twitter.com/2vRlZrA20R
— FBI Director Kash Patel (@FBIDirectorKash) October 7, 2025
NBC News reported:
The FBI took personnel action against three special agents who worked in connection with former special counsel Jack Smith’s probe of Donald Trump, firing at least two, three people familiar with the matter told NBC News.
All three agents were previously named in documents released by Sen. Chuck Grassley, R-Iowa, about “Arctic Frost,” an FBI probe that was the precursor to the Smith investigation, which resulted in two federal criminal cases against Trump: one for his handling of classified documents and the other involving his attempts to overturn his 2020 election loss, which ended in the Jan. 6 attack on the U.S. Capitol.
One of the fired FBI employees, a combat veteran who was months away from becoming eligible for retirement, was called back to the office after having left for the day and informed of the dismissal, a person familiar with the matter told NBC News. The other dismissed agent was also called back to the office after having left for the day, the person said.
The post NEW: FBI Fires Two Agents Who Worked For Jack Smith appeared first on The Gateway Pundit.
Politics
HUNGARIAN WITCH HUNT: After Ukraine Accused Orbán of Sending Drones Into Its Airspace, Now the European Union Is Investigating an Alleged Hungarian Spy Ring in Brussels

Ursula von de Leyen is coming for Viktor Orbán.
‘Everything is Hungary’s fault’.
There’s a new illness of the mind going around the Globalist corners of the European Union.
You can call it Hungarophobia or Magyarophobia, and it basically means that the conservative central European country is receiving the ‘Russian treatment’, with constant psyops and disinformation against it.
Around 10 days ago, Kiev regime leader Volodymyr Zelensky publicly accused Budapest of deploying multiple drones into Ukrainian airspace – a serious accusation never backed with any data, and soon dropped into oblivion.
Now, the Globalist archfoes of the European Union have broken another ‘sensational story’ against Viktor Orbán and his government.
Watch: Commission spokesperson Balázs Ujvári.
Orban has crossed a red line!
The European Commission probes Hungarian spy network in Brussels.According to reports that sparked the probe, the undercover spy ring allegedly operated under the cover of the Hungarian permanent representation, which at that time was led by… pic.twitter.com/Lc3oDaVG8a
— Yasmina (@yasminalombaert) October 9, 2025
Euronews reported:
“According to reports that sparked the probe, the undercover spy ring allegedly operated under the cover of the Hungarian permanent representation, which at that time was led by Olivér Várhelyi, who is now a European Commissioner.
The European Commission launched a probe on Thursday after several media reports alleged that the Hungarian secret services were trying to recruit EU employees in Brussels as informants.”
 Orbán is the man Globalists in Brussels love to hate.
Orbán is the man Globalists in Brussels love to hate.
The agents would have posed as diplomats of the Hungarian Permanent Representation to the EU in Brussels.
The spies allegedly targeted Hungarian staff at the European Commission.
“’We will be setting up an internal group to look into those allegations’, Commission spokesperson Balázs Ujvári said.
Earlier, Hungary’s Direct36, together with German outlet Paper Trail Media and Belgium’s De Tijd newspaper, reported that Hungarian intelligence services were allegedly trying to recruit Hungarians working in EU institutions to build a network.”
Read more:
Budapest Says Zelensky ‘Is Losing His Mind’ After Allegations of Hungarian Drones Invading Ukrainian Airspace
The post HUNGARIAN WITCH HUNT: After Ukraine Accused Orbán of Sending Drones Into Its Airspace, Now the European Union Is Investigating an Alleged Hungarian Spy Ring in Brussels appeared first on The Gateway Pundit.
Politics
House’s zero trust journey is more process than technology update

The House of Representatives started its journey to push security to the edge by first looking internally.
With hundreds of end points in member offices across the country, House technology leaders had to take stock of what cyber tools they were already using.
Jamie Crotts, the chief information officer for the House of Representatives, said that initial assessment of its current state of cyber tools and how they fit into the zero trust model was the first step in their improving the overall cyber posture of the lower chamber of Congress.
Jamie Crotts is the chief information officer for the House of Representatives.
“We plan on a three-year technology roadmap cycle. So it’s about understanding which step is the next best step to get us the most benefit for the architecture and for our users. And from that point, we adjusted our roadmap and our planning,” Crotts said on Ask the CIO. “We began budgeting for some of the larger items that are going to be more long term, and we began implementing things that we could do immediately, that were more quick wins, if you will, and that’s still where we are.”
While the House doesn’t have to meet the executive branch mandates under zero trust, Crotts said the maturity models developed by the Cybersecurity and Infrastructure Security Agency and Defense Department are helping to guide their efforts.
The initial zero trust assessment mapped against their current IT roadmap, which is broader than just cybersecurity, led to some adjustments for current and future planning as well as where to invest its limited budget.
Crotts said that mapping led the team to realize that achieving initial capabilities under zero trust was as much as about adjusting the way they did cybersecurity as it was about new tools.
“Looking at it from the users, devices, applications and the network, every single layer of that, we examined how our efforts were going to be able to make improvements. When we looked at the assessment and we saw we can get better at, say, provisioning of devices for users, we can do things a little bit differently that will get a slightly more secure device in their hands in a slightly faster time frame. That is something that would be low hanging fruit for us,” he said. “If it’s as simple as adjusting the way we do imaging to make sure it’s inclusive of certain types of tools, we would be able to take care of that without having to plan for a long-term investment that wasn’t already there. We’re not buying a new tool. We’re adjusting an existing process, and that’s most of our quick wins.”
Flexibility remains key to meeting cyber needs
At the same time, Crotts said they are optimizing existing cyber tools to push them closer key areas of zero trust.
“We spend a lot of money on these tools, whether they be cyber tools, specifically, monitoring analysis tools or general IT productivity tools, applications and suites. But we rarely take the time after we have purchased and implemented it to step back and say, ‘Are there other toggles we could adjust that give us a bit more benefit?’ So, part of our assessment from the zero trust side did exactly that,” he said. “It pointed out that we have some investments in tools giving us a bit of an overlap, which can result in a cost savings. If we identify turning on this widget and this tool actually allows us to stop buying this other tool, that’s a win. That’s essentially how we spent the last year, looking at the tools that we’ve already invested in reducing technical debt is something everybody’s trying to do. So every quick win we can get is amazing.”
Like most IT organizations, the House budgets on a multi-year cycle, so Crotts said they do their best to guess what cyber tools or IT applications they will need in a few years. He said having flexibility in existing tools and processes helps close gaps that otherwise they would have to wait for funding to address.
One example is how the House implemented cloud access security broker (CASB) capabilities.
“It might not be doing exactly what we want it to be doing, or we want to look at the way we do our web access firewalls a little bit differently or routing traffic differently coming from the far edge, things like that take a little bit more time,” he said. “We have to do that thorough analysis. We have to make an investment once we pick the right tool that’s going to work for our architecture. That’s really how we chalked up all of those things, so not necessarily by the pillar that they naturally belong in, but across all the pillars, where can we actually have the most innovative benefit for the House?”
With some initial zero trust capabilities implemented, Crotts said the next focus area is around the data pillar.
Focusing on the data pillar of zero trust
He said his team is spending a lot of time understanding their data governance model.
“Data is data, but the importance of that data is unique to the organization that creates it. Nowhere is that more true than in the legislative branch, where we have different types of data that other people don’t have to deal with, things like legislation data that’s protected by the Speech and Debate Clause of the Constitution. Those types of non-traditional data governance problems, if you will, are things that we’re trying to wrap our minds around,” Crotts said. “How do you do proper tagging of that kind of data? How do you understand the flow of that data throughout your enterprise? When it’s not as simple as tagging a Social Security Number automatically because I know what that looks like, but for some of these more ethereal concepts, it takes a real understanding.”
Crotts added that means analyzing current and possibly future tools to help manage the data as well as creating schemas that let data move securely and efficiently through the network.
“A lot of good security practices come back to the fundamentals of, can you invoke it in a policy and actually enforce it? So once we understand the data types in the data flow, and we get sort of the organizational agreement on, ‘Yes, these are the things and this is the level at which we want to want and need to protect them,’” he said. “Then setting up that structure becomes the next challenge, if you will. A lot of best security practices can be put in play there, but like everything else, you need to define it first.”
Once the House can define and manage its data, then applying a more strict version of privileged access management to further protect systems and data will be possible.
At the same time, Crotts said his team has to understand their users’ needs, of which there are thousands of people on Capitol Hill and across 900 district offices that need access to systems and data, to balance their experience with the cybersecurity requirements.
“A proper security tool configured well does not have to interrupt workflow. And that’s really key to understanding those challenges,” he said. “Every time a user has to stop and log into something else or authenticate or pull up their token numbers and reauthenticate, you have lost them. They become upset with the process, even if it’s perfectly efficient, you’ve interrupted them. You should only do that as little as possible. But then you need to trust that once they are logged into that session, that you’ve got the other controls in place to make sure that the accesses prevent them from moving laterally to a place where they shouldn’t be. If you’ve got all that in place, then you can trust that login and you don’t have to go through all those other processes.”
The post House’s zero trust journey is more process than technology update first appeared on Federal News Network.
-
 Entertainment7 months ago
Entertainment7 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment4 months ago
Entertainment4 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech7 months ago
The best sexting apps in 2025
-
 Entertainment6 months ago
Entertainment6 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech8 months ago
Tech8 months agoEvery potential TikTok buyer we know about
-
Tech8 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech8 months ago
Tech8 months agoAre You an RSSMasher?
-

 Politics8 months ago
Politics8 months agoDOGE-ing toward the best Department of Defense ever



