Politics
CISA must shift cyber defense toward a holistic endpoint protection and prevention strategy
Protecting critical infrastructure from ransomware and advanced cyberattacks is proving to be challenging across all sectors in the United States. In fact, these cyberattacks are growing in sophistication and are employing stealth techniques against common detection capabilities to remain undetected. The emergence of ransomware-as-a-service (RaaS) creates an elaborate ecosystem for leasing out malware and malicious software to affiliates and cybercriminals for profit. This allows ransomware actors to scale to increase profits and maximize their attack reach, while minimizing effort for ransomware developers. In fact, cybercriminals and nation state actors are blending and adopting tactics and techniques of each other, where espionage and cybercrime converge. What is common to both threat groups are evasion techniques, increasing the ability for these threat actors to remain in stealth mode, which makes it more difficult to detect.
Ransomware requires more protection
Cybercriminals who use RaaS can infect more victims, demand more ransoms, and improve their tactics to stay ahead of detection capabilities. According to Chainalysis, the Dark Angels ransomware group received the largest ransomware payment ever at approximately $75 million in 2024. Disrupting ransomware and advanced cyberattacks is imperative for national security. To do so will require industry to shift toward a holistic endpoint protection and prevention strategy that starts with endpoint privilege management (EPM). Why EPM? Because it is more resilient against ransomware and advanced cyberattacks, providing better protection capabilities to reduce the attack surface on endpoints. Endpoint detection and response (EDR) performance and detection against ransomware and advanced cyberattacks have failed to protect government agencies as cited in the Cybersecurity and Infrastructure Security Agency’s Red Team Assessment report. Moving to a holistic endpoint protection and prevention strategy will help shore up cyber defense for cyberattacks targeting critical infrastructure.
Threat actors bypassing EDR
Curated threat intelligence from MITRE ATT&CK and other threat intelligence sources have shown increasing use of advanced malware called EDR killers designed to evade, disable and manipulate EDR systems. EDR killers employ a range of techniques including terminating EDR security-related processes, tampering with EDR agents, DLL unhooking and API hooking, process hollowing and unloading kernel drivers. These evasion techniques pose a significant risk to critical infrastructure and government agencies responsible for critical infrastructure protection, rendering EDR capabilities ineffective and unreliable. Another common evasion technique highly weaponized by threat actors is living-off-the-land (LoTL) attacks that leverage native systems tools, trusted software and operating system (OS) utilities, such as PowerShell, Windows Management Instrumentation (WMI) and schedule tasks that are whitelisted by EDR.

Complimenting EDR with EPM protection capabilities is essential to combat highly sophisticated threat actors’ behaviors and activities. Understanding these gaps and issues in state-of-the-art practices is critical for elevating cyber defense with the right protection measures to boost cyber resiliency against evolving threats.
EDR leaves gaps in endpoint resiliency
Boosting cyber resiliency early in the ATT&CK lifecycle will disrupt threat actors’ capabilities and prevent them from increasing their foothold by evading detections and gaining privilege and persistence to move through the ATT&CK lifecycle. Early detection, which requires a more proactive approach, can prevent data exfiltration and impacts such as distributed denial of service, data destruction and encryption that are common with ransomware attacks. Shifting to a more proactive approach requires industry to rethink and adjust their endpoint security strategy that is less reliant on reactive capabilities associated with EDR capabilities. EDR by design focuses on detection and then prevention, which means it must accurately detect maliciousness before it can prevent the threat. That is good for common threats, but novel and sophisticated threats require longer attack chains before EDR can gain confidence.
This was demonstrated by security researchers who analyzed MITRE ATT&CK evaluation results over multiple years using whole-graph analysis to measure the performance of EDR systems. Specifically, various aspects were analyzed to include detection coverage, detection confidence, detection modifier, data source, etc. Security researchers identified the following gaps in EDR capabilities:
- Enhanced attack correlation — Many EDR systems still rely on detecting isolated events, and do not properly utilize comprehensive correlation to better understand and contextualize complex attack patterns. This limits the visibility in detection of multi-step and stealthy attack scenarios, which severely hamper response capabilities.
- EDR systems struggle with advanced techniques — Threats that employ techniques that use living-off-the-land and advanced evasion require more sophisticated correlation from EDR systems.
- Cross-host correlation is inconsistent — Many EDR systems struggle to detect lateral movement and coordinated attacks that span across multiple endpoints.
- EDR systems too Windows-centric – A large percentage of EDR systems do not support Linux-based endpoints; if they do, they result in low detection and protection results.
- Detection quality needs improvements — The variability in detection quality is essential for good coverage and detection. It is important to reduce the occurrence of low-quality alerts that can attribute to a considerable number of false positives — alert fatigue is real.
Cyber defenders must understand gaps in their overall security posture and develop strategies to elevate their cyber defense. To do that, a holistic endpoint strategy is needed to help reduce the attack surface on endpoints by managing privileges at the individual, user group and application levels. In the context of zero trust, no end user has privilege access by default. Privilege access is granted using just-in-time (JIT), to ensure just enough access, on an as-needed basis.
Closing gaps left by EDR
Enforcing least privilege, JIT and just enough access capabilities with endpoint privilege management provides protection and prevention capabilities that EDR lacks and cannot perform natively. These protection and prevention capabilities are designed to restrict elevated rights and control application execution. Implementing EPM with EDR allows critical infrastructure and government agencies to achieve stronger endpoint resiliency.
- EPM reduces the noise by limiting user privileges and application execution, which allows EDR to improve accuracy and threat detection.
- EPM limits the scope of potential damage, which allows EDR to focus on investigating and remediating specific threats to accelerate incident response.
- EPM prevents tampering with EDR agents by removing standing privileges and stopping privilege escalation attempts, which ensures EDR can continue to operate on a compromised endpoint.
- EPM contextualizes users and applications with elevated privileges, which improves threat hunting, enabling security teams to prioritize and investigate most likely threats.
CISA has been tracking ransomware actors and various techniques used to bypass and evade EDR. As part of their #StopRansomware campaign, CISA has been diligent about providing threat intelligence to the community with respect to tradecraft used by threat actors. CISA within the last four months has updated or released advisories for some of the top ransomware gangs outlining their ATT&CK techniques used in the wild.
- Play (Advisory updated June 4, 2025)
- Rhysida (Advisory updated April 30, 2025)
- Medusa (Published March 2025)
- Ghost aka Cringe (Published February 2025)
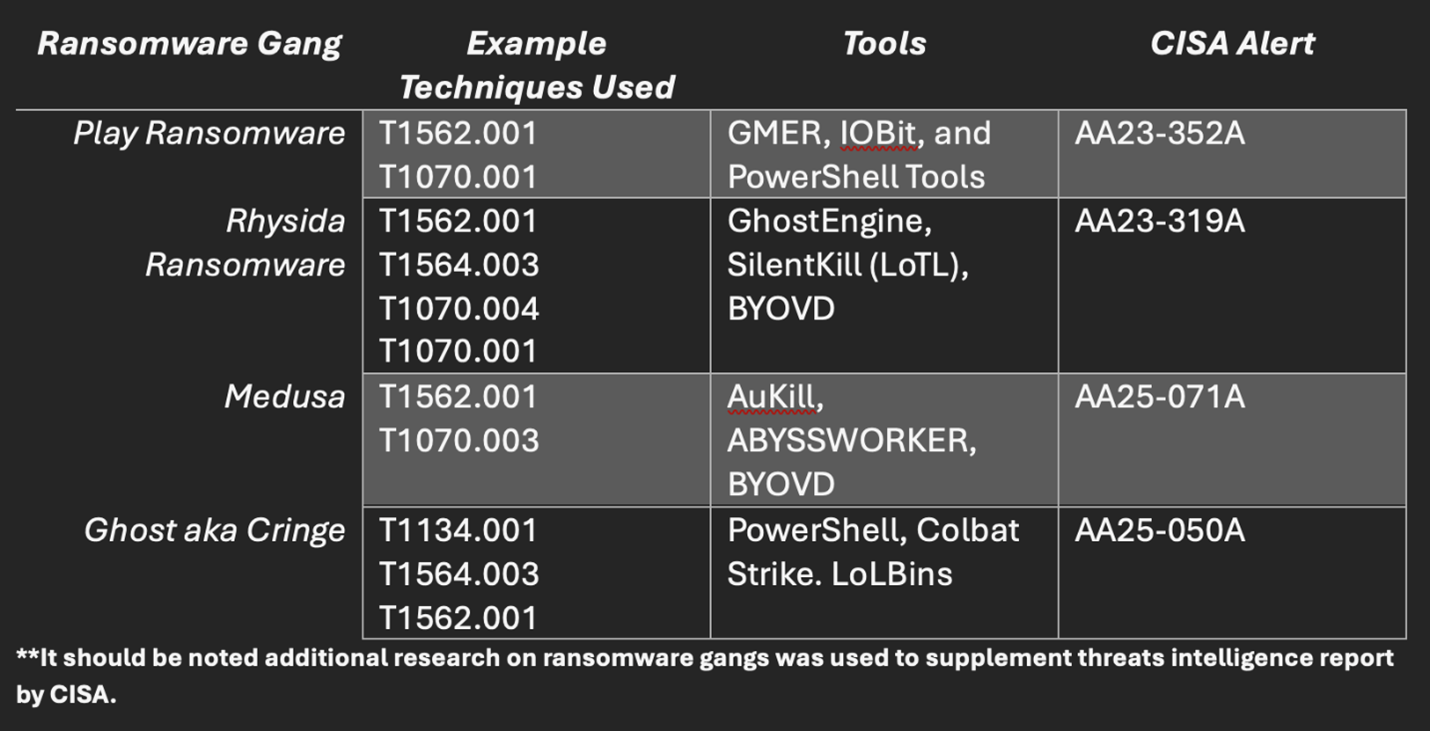
The table above highlights the evasion and bypass techniques that were used and have been associated with ransomware attacks. Threat actors are actively using LoTL and bring-your-own-vulnerable-driver (BYOVD) more in their attack arsenal. This illustrates the growing use of EDR evasion and bypass techniques by popular and active ransomware, but also demonstrates the need to complement other endpoint protection capabilities like EPM to boost endpoint resiliency. This echoes CISA’s Red Team assessment report, citing that the red team excelled in bypassing EDR solutions by avoiding the use of basic “known-bad” detections the tools would capture. In fact, the report further states that EDR detected only a few of the red team’s payloads in the organization’s Windows and Linux environments.
Defining a holistic endpoint protection and prevention strategy
A holistic endpoint protection and prevention strategy leaves no privileges behind. Privileges that are left behind become prime attack vectors that threat actors use to bypass and evade detection capabilities deployed in the environment to establish persistence and move laterally. Industry must pivot from a single point of failure with EDR, to a more holistic approach that not only enhances and protects EDR but can disrupt threat actors early in the ATT&CK lifecycle by enforcing privilege management to reduce the attack surface and harden the endpoint system. Enforcing least privilege, JIT and just enough access capabilities with endpoint privilege management provides protection and prevention capabilities that EDR lacks and cannot perform natively. EPM embraces foundational zero trust principles and concepts which will allow government agencies to mature their zero trust, while elevating their cyber defense.
Kevin E. Greene is chief security strategist for the public sector at BeyondTrust.
The post CISA must shift cyber defense toward a holistic endpoint protection and prevention strategy first appeared on Federal News Network.
Politics
President Trump Taps Dr. Ben Carson for New Role — A HUGE Win for America First Agenda

Dr. Ben Carson is the newest member of the Trump administration.
On Wednesday, former Secretary of the Department of Housing and Urban Development, Ben Carson, was sworn in as the national adviser for nutrition, health, and housing at the U.S. Department of Agriculture.
Agriculture Secretary Brooke Rollins shared that Carson’s role will be to oversee Trump’s new Big Beautiful Bill law, which aims to ensure Americans’ quality of life, from nutrition to stable housing.
After being sworn in, Carson shared, “Today, too many Americans are suffering from the effects of poor nutrition. Through common-sense policymaking, we have an opportunity to give our most vulnerable families the tools they need to flourish.”
WATCH:
BREAKING Dr. Ben Carson has been sworn in as the National Nutrition Advisor to Make America Healthy Again
THIS IS A HUGE WIN pic.twitter.com/Dr5AsSDkRM
— MAGA Voice (@MAGAVoice) September 24, 2025
Per USDA:
Today, U.S. Secretary of Agriculture Brooke L. Rollins announced that Dr. Benjamin S. Carson, Sr., M.D., was sworn in as the National Advisor for Nutrition, Health, and Housing at the U.S. Department of Agriculture (USDA).
“There is no one more qualified than Dr. Carson to advise on policies that improve Americans’ everyday quality of life, from nutrition to healthcare quality to ensuring families have access to safe and stable housing,” said Secretary Rollins.
“With six in ten Americans living with at least one chronic disease, and rural communities facing unique challenges with respect to adequate housing, Dr. Carson’s insight and experience is critical. Dr. Carson will be crucial to implementing the rural health investment provisions of the One Big Beautiful Bill and advise on America First polices related to nutrition, health, and housing.
“As the U.S. Secretary of Housing and Urban Development in the first Trump Administration, Dr. Carson worked to expand opportunity and strengthen communities, and we are honored to welcome him to the second Trump Administration to help lead our efforts here at USDA to Make America Healthy Again and ensure rural America continues to prosper.”
“Today, too many Americans are suffering from the effects of poor nutrition. Through common-sense policymaking, we have an opportunity to give our most vulnerable families the tools they need to flourish,” said Dr. Ben Carson. “I am honored to work with Secretary Rollins on these important initiatives to help fulfill President Trump’s vision for a healthier, stronger America.”
On Sunday, Dr. Carson was one of the many speakers at the memorial service of the late TPUSA founder Charlie Kirk.
During the memorial service, Carson highlighted that Kirk was shot at 12:24 p.m. and then continued to share the Bible verse John 12:24, which reads, “Verily, verily, I say unto you, Except a corn of wheat fall into the ground and die, it abideth alone: but if it die, it bringeth forth much fruit.”
WATCH:
Ben Carson reads John 12:24 at the Charlie Kirk’s funeral. Charlie was shot at 12:24.
It reads: “Very truly I tell you, unless a kernel of wheat falls to the ground and dies, it remains only a single seed. But if it dies, it produces many seeds”
God is moving and speaking. pic.twitter.com/0ZbVTAwwYl
— Danny Botta (@danny_botta) September 21, 2025
The post President Trump Taps Dr. Ben Carson for New Role — A HUGE Win for America First Agenda appeared first on The Gateway Pundit.
Politics
LEAKED MEMO: Deep State Prosecutors in the Eastern District of Virginia Claim There Isn’t Enough Evidence to Convict Comey Amid Reports of Imminent Indictment


On Wednesday evening, disgruntled officials in the Eastern District of Virginia leaked contents of a memo explaining why charges should not be brought against James Comey.
As reported earlier, former FBI Director James Comey is expected to be indicted in the Eastern District of Virginia in the next few days.
Comey will reportedly be charged for lying to Congress in a 2020 testimony about whether he authorized leaks to the media.
Officials in the Eastern District of Virginia are still fighting to stop Comey from being charged after Trump fired US Attorney Erik Siebert.
President Trump last week fired Erik Siebert as the US Attorney for the Eastern District of Virginia because he refused to bring charges against Letitia James, Comey, Schiff and others.
On Saturday evening, President Trump announced that he had appointed Lindsey Halligan – his personal attorney who defended him against the Mar-a-Lago raid – as US Attorney for the Eastern District of Virginia.
Now, with just days to go before the statute of limitations runs out to charge Comey for lying during a September 30, 2020 testimony, Lindsey Halligan is reportedly gearing up to indict Comey.
Prosecutors reportedly gave newly sworn-in Halligan a memo defending James Comey and explaining why charges should not brought against the fired FBI Director.
Per MSNBC’s Ken Dilanian:
Two sources familiar with the matter tell me prosecutors in the EDVA US attorney‘s office presented newly sworn US attorney Lindsey Halligan with a memo explaining why charges should not be brought against James Comey, because there isn’t enough evidence to establish probable cause a crime was committed, let alone enough to convince a jury to convict him.
Justice Department guidelines say a case should not be brought unless prosecutors believe it’s more likely than not that they can win a conviction beyond a reasonable doubt.
Two sources familiar with the matter tell me prosecutors in the EDVA US attorney‘s office presented newly sworn US attorney Lindsey Halligan with a memo explaining why charges should not be brought against James Comey, because there isn’t enough evidence to establish probable…
— Ken Dilanian (@DilanianMSNBC) September 24, 2025
The post LEAKED MEMO: Deep State Prosecutors in the Eastern District of Virginia Claim There Isn’t Enough Evidence to Convict Comey Amid Reports of Imminent Indictment appeared first on The Gateway Pundit.
Politics
Nearly 8 in 10 Voters Say the United States is in Political Crisis After the Assassination of Charlie Kirk

Nearly eight in ten voters believe that the United States is in a political crisis in the wake of the assassination of conservative icon Charlie Kirk.
According to a Quinnipiac University national poll of registered voters released on Wednesday, a massive 93 percent of Democrats, 84 percent of independents, and 60 percent of Republicans said the nation is in a political crisis.
“The Kirk assassination lays bare raw, bipartisan concerns about where the country is headed,” Quinnipiac University Polling Analyst Tim Malloy said of the poll results.
Quinnipiac reports:
Seventy-one percent of voters think politically motivated violence in the United States today is a very serious problem, 22 percent think it is a somewhat serious problem, 3 percent think it is a not so serious problem, and 1 percent think it is not a problem at all.
This is a jump from Quinnipiac University’s June 26 poll when 54 percent thought politically motivated violence in the United States today was a very serious problem, 37 percent thought it was a somewhat serious problem, 6 percent thought it was a not so serious problem, and 2 percent thought it was not a problem at all.
Nearly 6 in 10 voters (58 percent) think it will not be possible to lower the temperature on political rhetoric and speech in the United States, while 34 percent think it will be possible.
Over half, 54 percent, of voters believe the US will see increased political violence over the next few years. Another 27 percent said they think it will stay “about the same,” while just 14 percent believe it will ease.
A 53 percent majority also said they are “pessimistic about freedom of speech being protected in the United States.”
Surprisingly, a 53 percent majority also believes the current system of democracy is not working.
“From a perceived assault on freedom of speech to the fragility of the democracy, a shudder of concern and pessimism rattles a broad swath of the electorate. Nearly 80 percent of registered voters feel they are witnessing a political crisis, seven in ten say political violence is a very serious problem, and a majority say this discord won’t go away anytime soon,” Malloy added.
The vast majority, 82 percent, said the way that people discuss politics is contributing to the violence.
“When asked if political discourse is contributing to violence, a rare meeting of the minds…Republicans, Democrats, and independents in equal numbers say yes, it is,” Malloy said.
The survey was conducted from September 18 to 21 among 1,276 registered voters with a margin of error of +/- 3.3 percentage points.
The post Nearly 8 in 10 Voters Say the United States is in Political Crisis After the Assassination of Charlie Kirk appeared first on The Gateway Pundit.
-
 Entertainment6 months ago
Entertainment6 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment3 months ago
Entertainment3 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech6 months ago
The best sexting apps in 2025
-
 Entertainment5 months ago
Entertainment5 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech7 months ago
Tech7 months agoEvery potential TikTok buyer we know about
-
Tech7 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech7 months ago
Tech7 months agoAre You an RSSMasher?
-

 Politics7 months ago
Politics7 months agoDOGE-ing toward the best Department of Defense ever





