Politics
Arrington kicks off effort to eliminate RMF for DoD software

The Defense Department’s latest effort to obtain secure software kicked off a 90-day sprint today to develop a framework and implementation plan under the Software Fast Track (SWFT) initiative.
Katie Arrington, who is performing the duties of the DoD chief information officer, officially launched the initiative in a much-anticipated memo signed on April 24. The Pentagon only made the memo public today.
At the same time, the DoD CIO’s office released three requests for information (RFIs) under SWFT asking vendors for insights around tools, external assessments and how to best use automation and artificial intelligence to assist DoD-led risk assessment for expedited cybersecurity authorizations.
Katie Arrington is performing the duties of the DoD CIO.
“Instead of going through the arduous process of finding a program manager who will look at your software, send it to a lab and test it, I’m of a modern age. In the Supplier Performance Risk System (SPRS), it is backed by a platform called Enterprise Mission Assurance Support Service (eMASS). eMASS is approved from [unclassified] all the way up to special access program (SAP). What I’m going to have software providers do is provide me with their base risk scores on the DoD’s 12 characteristics of risk that range from financial to foreign ownership, control or influence (FOCI) to cyber, including the Cybersecurity Maturity Model Certification (CMMC) and onward down,” Arrington said at the recent AFCEA DC lunch on April 23.
“I’m going to ask you, if you’re a software provider, to provide me your software bill of materials (SBOM) in both your sandbox and production, along with a third-party SBOM. You’re going to populate those artifacts into eMASS. I will have AI tools on the back end to review the data instead of waiting for a human and if all of it passes the right requirements, provisional authority to operate (ATO). Here’s the better part, because I’m blowing up the risk management framework (RMF) and I’m blowing up the ATOs. They’re stupid. They’re archaic,” she said.
As part of the dismantling of the RMF, Arrington brought together on May 1 all service and agency CIOs and chief information security officers to determine what are the security questions and answers that matter the most.
“I want the RMF eliminated. It can be the framework we base it on, but I only have five things I really care about. Did you develop what you’re doing in secure by design? How do I validate that? Are you working with zero trust? How do I validate that? What’s more important in ATO or continuous monitoring? Continuous monitoring, so how do I do that?” she said. “After the May event, we’ll come back and then I’m going to ask industry, ‘does it make sense?’ As we’re redoing acquisition reform, we’re re looking at how to do the far why shouldn’t we be looking at the RMF, which is the thing that holds everything together, and it’s the most archaic thing in the world.”
New attempt to move toward continuous ATO
DoD moved to the RMF in 2018 when it transitioned away from the DoD Information Assurance Certification and Accreditation Process (DIACAP). The RMF is a unified framework for assessing organizational risk posed by IT systems and managing that risk by selecting the appropriate security controls. The framework supports continuous assessment as the security status changes throughout the system lifecycle.
Over time, however, the RMF became too static and unable to guarantee the security of a system. DoD tried to promote the concept of continuous authority to operate (cATO) in a 2022 memo from the CIO. The concept focused on enabling system owners to show they’re capable of defending their systems in real-time and that they have a secure software supply chain.
The Navy, for example, has been moving away from the RMF for more than three years with the “Cyber Ready” approach, which focuses instead on continuous monitoring and ongoing risk assessments. Former Navy Secretary Carlos Del Toro announced the “Cyber Ready” initiative in August 2022 in a memo outlining its principles of pre-emptive cyber defense.
The SWFT initiative is Arrington’s attempt to finally move DoD, particularly software that the military buys to this cATO approach.
“I remember when we were going from DICAP to RMF, I wanted to pull my hair out. It’s still paper. Who reads it? What we do is a program protection plan? We write it, we put it inside the program. We say, ‘this is what we’ll be looking to protect the program.’ We put it in a file, and we don’t look at it for three years,” she said. “We have to get away from paperwork. We have to get away from the way we’ve done business to the way we need to do business, and it’s going to be painful, and they’re going to be a lot of things that we do, and mistakes will be made. I really hope that industry doesn’t do what industry tends to do is want to sue the federal government instead of working with us to fix the problems. I would really love that.”
Along with the memo, Arrington’s office released three RFIs to gauge industry insights and feedback for how to make the process work best.
The first RFI is for SWFT tools.
“DoD seeks industry perspectives for SWFT risk criteria for consistent, secure and accelerated risk assessments. The SWFT supply chain risk management (SCRM) requirements will equip DoD authorization officials with product-specific risk information throughout the software development life cycle,” DoD wrote in the RFI.
DoD seeks answer to six questions, including:
- What are the specific references or industry standards organizations rely on when considering secure software development and software supply chain threats and vulnerabilities to a company and its software products?
- What artifacts does your organization produce to perform risk assessments of software? Does your organization use automated tools to produce these artifacts?
The second RFI is for external assessments to streamline the processes.
“DoD seeks industry perspectives that utilize existing external assessment methodologies that can serve the SWFT initiative. These external assessment methodologies must support rigorous software security verification processes and enable DoD-led risk determinations,” DoD wrote.
DoD laid out five questions, including:
- Does your organization currently have an audit function that assesses software security? If so, internal or external? And is this assessment performed as part of another compliance regime? Which one(s)?
- How could a SWFT external assessment demonstrate technical expertise, cybersecurity, and supply chain risk management (SCRM) experience that is inclusive of sensitive data protection, impartiality, and independence?
The third RFI is how best to apply automation and AI tools to the assessments.
“DoD seeks industry perspectives for the use of automation and artificial intelligence to assist DoD-led risk assessment for expedited cybersecurity authorizations. Risk assessment assistance will utilize supplier SBOM, SWFT artifacts and attestations, and DoD-specific knowledge (e.g., mission impact determinations),” DoD wrote.
Industry has only four questions to answer in this RFI, including:
- What are the possible ways that automation or AI could assist to streamline DoD-led SWFT risk assessments under the DoD defined Risk Management Framework (RMF)?
- What are the considerations that DoD should prioritize when evaluating automation and AI solutions for DoD-led SWFT risk assessments and determinations?
Responses to all three RFIs are due by May 20.
“This initiative will lead the department’s adoption in best practices to obtain, develop and field secure software,” Arrington wrote in the memo. “The SWFT initiative will define clear, specific cybersecurity and SCRM requirements, rigorous software security verification processes, secure information sharing mechanisms and federal government-led risk determinations to expedite the cybersecurity authorizations for rapid software adoption.”
The post Arrington kicks off effort to eliminate RMF for DoD software first appeared on Federal News Network.
Politics
Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle

Screencap of YouTube video.
A Black Lives Matter activist in Boston named Monica Cannon-Grant pleaded guilty to federal charges this week, admitting that she scammed donors and used their money to fund her own lavish lifestyle.
Cannon-Grant was previously held up as an admired figure. The city of Boston named her the Bostonian of the year at one point for her ‘social justice activism’ and she was even recognized by the Boston Celtics basketball team for her efforts.
She is now facing a minimum of two years in prison.
The New York Post reports:
BLM-linked activist admits conning donors to fund her lavish lifestyle
A once-celebrated Boston social activist has pleaded guilty to defrauding donors — including Black Lives Matter — out of thousands of dollars that she used as a personal piggy bank.
Monica Cannon-Grant, 44, pleaded guilty Monday to 18 counts of fraud-related crimes that she committed with her late husband while operating their Violence in Boston (VIB) activists group, according to the US Attorney’s Office in Massachusetts.
The activist scammed money — including $3,000 from a BLM group — while claiming it was to help feed children and run protests like one in 2020 over the murder of George Floyd and police violence.
Cannon-Grant also conned her way into getting $100,000 in federal pandemic-related unemployment benefits — which she used to pay off her personal auto loan and car insurance policy.
But she has now confessed to transferring funds to personal bank accounts to pay for rent, shopping sprees, delivery meals, visits to a nail salon — and even a summer vacation to Maryland.
Just amazing.
Monica Cannon-Grant stole from donors, scammed the government, and lived it up while preaching about oppression. BLM grift is the only nonprofit where fraud is part of the mission statement. https://t.co/ir3q9lqYrh
— Matthew Newgarden (@a_newgarden) September 23, 2025
BREAKING: BLM activist Monica Cannon-Grant pleads guilty to 27 fraud charges, misusing over $1M from Violence in Boston for personal gain. Echoes Sir Maejor Page’s $450K scam conviction. A wake-up call for nonprofit accountability. pic.twitter.com/N9vvD369gB
— (@pr0ud_americans) September 14, 2025
Here’s a local video report:
She should pay back every penny.
The post Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle appeared first on The Gateway Pundit.
Politics
Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO)

As the Gateway Pundit reported yesterday, former MSNBC host and generally unhinged leftist Keith Olbermann, appeared to threaten CNN’s conservative pundit Scott Jennings on Twitter saying, ‘You’re next motherf**ker.’
Well, Olbermann may have gotten a phone call or a visit from the FBI because today he walked back those comments with a full-throated apology.
RedState has an update:
To quickly recap, Scott Jennings, a Salem Media Network radio host and conservative CNN political commentator, reacted to breaking news on Monday that Kimmel had been reinstated by tweeting, “So basically his employer suspended him for being an insensitive pr**k, and we don’t live in an authoritarian regime? Got it.”
This enraged Olbermann, who proceeded to tweet what many, including Jennings, perceived to be a threat. “You’re next, motherf**ker. But keep mugging to the camera.” Jennings tagged Patel and included a screengrab of the tweets in response.
Though the FBI hasn’t commented as to whether an investigation was launched, Olbermann ostensibly appears to have thought twice about what he tweeted and deleted, apologizing profusely in tweets posted on Tuesday and claiming what he wrote was “misinterpreted”:
See Olbermann’s tweet below:
I apologize without reservation to @ScottJenningsKY
Yesterday I wrote and immediately deleted 2 responses to him about Kimmel because they could be misinterpreted as a threat to anything besides his career. I immediately replaced them with ones specifying what I actually meant. pic.twitter.com/SPWLb73nEk
— Keith Olbermann (@KeithOlbermann) September 23, 2025
I oppose and condemn political violence, and the threat of it. All times are the wrong time to leave even an inadvertent impression of it – but this time is especially wrong
I should've acknowledged the deletion and apologized yesterday. I'm sorry I delayed.
— Keith Olbermann (@KeithOlbermann) September 23, 2025
Scott Jennings, always a class act, offered this hilarious response:
SCOTT JENNINGS: “Marking myself SAFE from that NUT, Keith Olbermann!” pic.twitter.com/EYZX6vm5Oh
— Dustin Grage (@GrageDustin) September 23, 2025
Keith Olbermann really needs help. The guy is just so out of control.
The post Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO) appeared first on The Gateway Pundit.
Politics
Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished

 Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson lived with his transgender partner – a male-to-female trans named Lance “Luna” Twiggs.
The FBI used Robinson’s texts with his transgender partner to solidify that Robinson was the assassin. Lance Twiggs has not been charged with any crime; however, federal authorities are still investigating.
Last week, Utah authorities released the text exchange between Tyler Robinson and his transgender lover, Lance Twiggs, sent shortly after Kirk’s assassination.
Utah County District Attorney Jeff Gray announced seven charges against Charlie Kirk assassin Tyler Robinson. They will also be seeking the death penalty.
Robinson was charged with:
– Count 1: Aggravated murder (capital offense)
– Count 2: Felony reckless discharge of a firearm causing bodily injury
– Count 3: Felony obstruction of justice for hiding the firearm
– Count 4: Felony obstruction of justice for discarding the clothing he wore during the shooting
– Count 5: Witness tampering for asking roommate to delete incriminating messages
– Count 6: Witness temperating for demanding trans roommate stay silent, and not speak to police
– Count 7: Commission of a violent offense in the presence of a child
Jeff Gray released the chilling texts between Tyler Robinson and his “love” Lance Twiggs.
Read the text exchange here:
 Tyler Robinson texts with transgender lover Lance Twiggs / 1
Tyler Robinson texts with transgender lover Lance Twiggs / 1
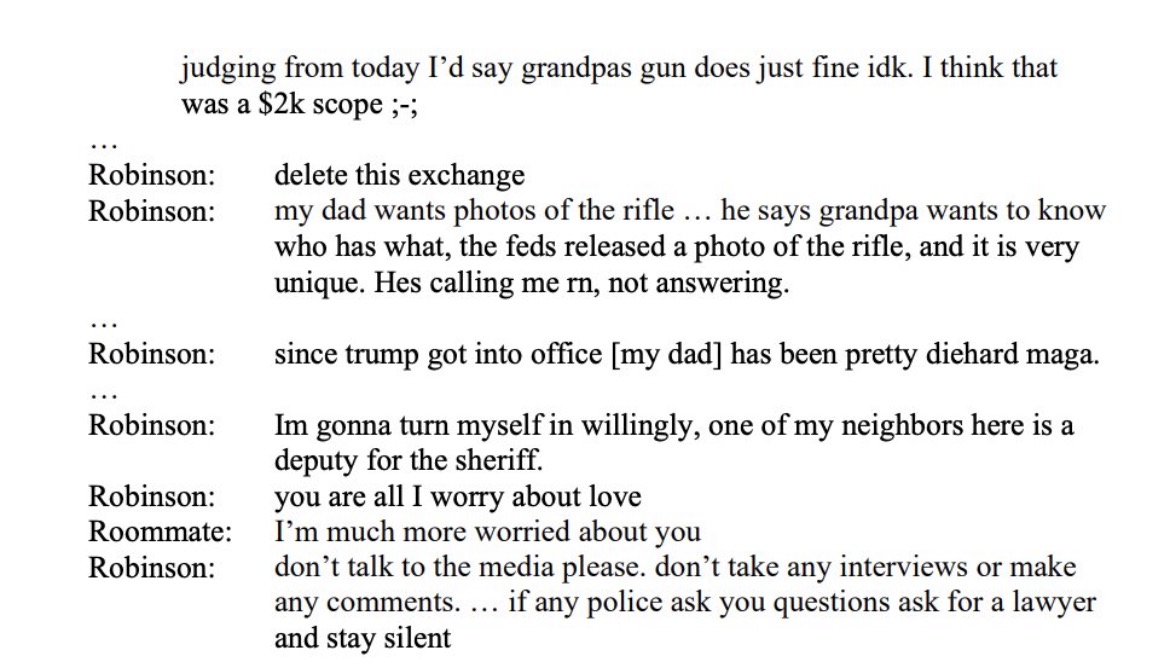 Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Lance Twiggs was reportedly cooperating with the FBI, however, according to the Daily Mail he has seemingly vanished.
“If [Lance Twiggs] ever comes back, it will be in a body bag,” a neighbor said to the Daily Mail. “That’s not a threat – I’m just saying that there are so many people who want a piece of him he’d be mad to show his face in public again. This was a generational event.”
The Daily Mail reported:
The Trans boyfriend of Charlie Kirk’s alleged assassin has fled their former lovenest – and locals tell the Daily Mail they never want to see him again.
Lance Twiggs, 22, was led away for questioning when police swooped on the smart three-bed condo he shared with accused gunman Tyler Robinson, 22.
Shaken neighbors say the part time plumber has not been back to the $320,000 property in St. George, Utah – one declaring: ‘Good riddance. I never want to see either of them again.’
His beaten-up Infinity compact is still parked in his space with his work gear tossed across the back seat and a sandwich wrapper and a drink on the front passenger seat.
Upstairs lights have been left on for more than a week and notes and Amazon packages are piling up outside the home owned by Twiggs’s devout Mormon family.
The post Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished appeared first on The Gateway Pundit.
-
 Entertainment6 months ago
Entertainment6 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment3 months ago
Entertainment3 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech6 months ago
The best sexting apps in 2025
-
 Entertainment5 months ago
Entertainment5 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech7 months ago
Tech7 months agoEvery potential TikTok buyer we know about
-
Tech7 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech7 months ago
Tech7 months agoAre You an RSSMasher?
-

 Politics7 months ago
Politics7 months agoDOGE-ing toward the best Department of Defense ever



