Politics
Public Service Recognition Week comes as many feds face difficult career decisions
Each year, Public Service Recognition Week is a time to show civil servants support for the often under-recognized and incredibly difficult task of delivering services to the public — like the Social Security employee who’s processing a mountain of paperwork to distribute benefits, or the HR specialist who’s managing the complicated requirements involved in shuffling federal employees into, out of and between positions.
But the recognition federal employees are receiving this week is cast against a much darker backdrop this year. It comes as the Trump administration attempts to significantly shrink and reconfigure the federal workforce at a pace and scale not seen in recent memory, maybe ever.
As a result, federal employees have been heading for the exits in droves — either by choice or by force. The administration fired tens of thousands of probationary employees, then later reinstated them, then reversed course once again. And agencies are in the process of eliminating a number of federal positions as part of reductions in force (RIFs), all under the directions of the White House.
At the same time, many federal employees are grappling with the nearly impossible decision of whether to leave their jobs on their own terms through the relaunched deferred resignation program (DRP) or stick it out in the hopes that their positions are still standing after RIFs take place across agencies.
Back in February, about 75,000 federal employees governmentwide applied for the first round of the DRP, according to the Trump administration. But the number of second-round DRP applications, as well as those being accepted into the program, have without a doubt gone up — although we don’t yet know the final tallies.
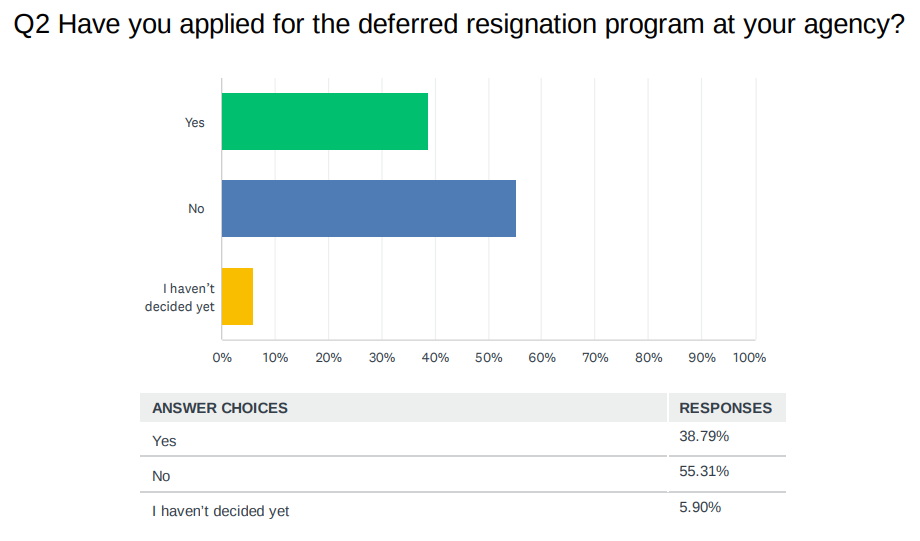
In an online survey conducted in April, Federal News Network heard from more than 4,500 federal employees on either why they decided to apply for a deferred resignation through their agency, or why they chose to “hold the line.” Out of the survey respondents, nearly 40% said they applied for the DRP at their agency, agreeing to quit their jobs now in exchange for several months of pay. Federal News Network’s survey is non-scientific, meaning that the results do not necessarily reflect the actual numbers of federal employees applying for the DRP.
Source: Federal News Network April 2025 deferred resignation survey of about 4,500 federal employees. The survey is a non-scientific survey of respondents who were self-selected.
With the Office of Personnel Management’s governmentwide “fork in the road” offer earlier this year, many employees said they didn’t apply for a deferred resignation for a number of reasons. Many didn’t trust OPM to follow through on the offer. Others said it felt like they were giving into the Trump administration’s wishes. And still others wanted to keep their jobs out of dedication to their agency’s mission.
Whatever the reason may have been, our survey results showed that nearly 70% of respondents did not consider taking a deferred resignation and did not apply for it in the first round of the offer.
But now reading the tea leaves more closely, many more employees have chosen to exit their jobs on their own terms, rather than face a possibility of being forced out anyway in a RIF. About 70% of respondents in Federal News Network’s survey said they are seeing more of their colleagues take the DRP in the second round.
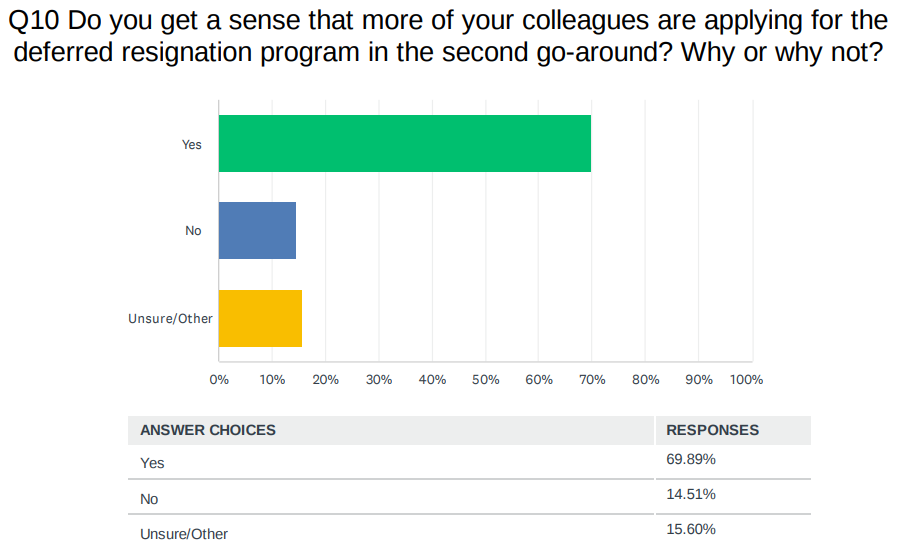 Source: Federal News Network April 2025 deferred resignation survey of about 4,500 federal employees. The survey is a non-scientific survey of respondents who were self-selected.
Source: Federal News Network April 2025 deferred resignation survey of about 4,500 federal employees. The survey is a non-scientific survey of respondents who were self-selected.
“A sinking ship”
The reasons more federal employees now want to apply for the DRP, however, still vary greatly. The survey results show a combination of federal employees who were worried about RIFs, burnt out from the growing pressure coming from the Trump administration or whose initial reservations about the legitimacy of the DRP have been alleviated.
“By now, more employees might have had the time to fully understand the program’s benefits and conditions, making them feel more confident about their decision,” one survey respondent observed. “Any initial skepticism about the program might have faded as employees saw that the promised benefits were delivered to those who participated in the first round.”
In the first round of the deferred resignation program, some saw the risk of leaving as greater than the risk of staying. Now, that feeling has reversed for many.
“People are seeing the reality of the RIF happening in front of them in different parts of the agency and it has become very real,” one employee noted.
Many respondents felt that applying for the second round of the DRP kept their decision in their own hands, rather than leaving it to the agency to determine whether they’d keep their positions. As one survey respondent put it, in comparison to an agency RIF, the DRP is “the lesser of two evil options.”
“I initially thought it was too risky to take the DRP when it was first offered. I believed I’d be able to keep my job,” another respondent wrote. “However, by the time the second DRP was offered, I realized how unstable the government was and that I might lose my position.”
Another respondent wrote, “People were more desperate and afraid of losing their jobs after seeing what happened to the probationary employees. The nature of our work and the makeup of the federal government are changing, and many people were not willing to stay aboard what they perceive as a sinking ship.”
And like many feds these days, one respondent said they made the tough choice to leave public service after spending 20 years in the federal workforce.
“Morale is low and stress is high. Work volumes will increase for those who remain. The daily grind in the current environment is not worth it anymore,” the respondent wrote. “After all, we were just dismissed and made to feel replaceable despite so much dedication to our public service mission for many years.”
Dedication to public service holds strong
Depending on where federal employees are in their career also appears to have an influence on their decision to apply for the second round of the DRP. In the survey, many employees close to retirement, as well as many within the first few years of their careers, saw themselves as ones on the cusp of the finish line, or ones who would be the first to go in a RIF.
“I’m close to retirement anyway and the administration is destroying my agency,” one respondent wrote.
Another said, “I was already terminated as a probationary employee and was confident that I would be terminated during the upcoming RIF.”
Those in the middle of their careers — who are still a ways away from retirement, but tenured enough that they have a better chance of surviving a RIF — may be more likely to choose to stay in their jobs for the time being.
Still, it may be a while before there’s a complete picture of how many federal employees chose to leave their jobs, and for what reason. Many agencies are still sifting through the deferred resignation paperwork to determine who will be accepted into the program, and who will be considered ineligible.
But at least at one agency, the numbers are incredibly telling. The IRS received deferred resignation applications from a whopping 22,000 employees — about one-quarter of the agency’s entire workforce. The IRS later denied about 10% of the employees who applied for the DRP offer. That leaves some 20,000 employees who are expected to walk out the door.
Despite many feds vacating their positions, many others are choosing to stay and weather the storm. That decision also has a wide variety of reasons behind it — some spoke of a need for financial stability or concerns about a tumultuous job market.
But in what feels like an homage to Public Service Recognition Week, federal employees who are staying put said they are choosing to remain hopeful about the future of the civil service and continuing to serve the public as they have for years.
One federal employee who took the survey said they are staying “simply because I don’t want to resign from public service. I refuse to let threats and harassment rule my decision-making about my career.”
Another employee wrote, “I am a public servant and while times are tough, I’m committed to my job and public service.”
And still another respondent said, “It was a tough decision, and I’ve been swinging back and forth for days about what to do. But ultimately what tipped the scale is that I do take pride in my work, and walking away from that was a heartbreaking thought, even with everything I’m being put through.”
The post Public Service Recognition Week comes as many feds face difficult career decisions first appeared on Federal News Network.
Politics
Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle

Screencap of YouTube video.
A Black Lives Matter activist in Boston named Monica Cannon-Grant pleaded guilty to federal charges this week, admitting that she scammed donors and used their money to fund her own lavish lifestyle.
Cannon-Grant was previously held up as an admired figure. The city of Boston named her the Bostonian of the year at one point for her ‘social justice activism’ and she was even recognized by the Boston Celtics basketball team for her efforts.
She is now facing a minimum of two years in prison.
The New York Post reports:
BLM-linked activist admits conning donors to fund her lavish lifestyle
A once-celebrated Boston social activist has pleaded guilty to defrauding donors — including Black Lives Matter — out of thousands of dollars that she used as a personal piggy bank.
Monica Cannon-Grant, 44, pleaded guilty Monday to 18 counts of fraud-related crimes that she committed with her late husband while operating their Violence in Boston (VIB) activists group, according to the US Attorney’s Office in Massachusetts.
The activist scammed money — including $3,000 from a BLM group — while claiming it was to help feed children and run protests like one in 2020 over the murder of George Floyd and police violence.
Cannon-Grant also conned her way into getting $100,000 in federal pandemic-related unemployment benefits — which she used to pay off her personal auto loan and car insurance policy.
But she has now confessed to transferring funds to personal bank accounts to pay for rent, shopping sprees, delivery meals, visits to a nail salon — and even a summer vacation to Maryland.
Just amazing.
Monica Cannon-Grant stole from donors, scammed the government, and lived it up while preaching about oppression. BLM grift is the only nonprofit where fraud is part of the mission statement. https://t.co/ir3q9lqYrh
— Matthew Newgarden (@a_newgarden) September 23, 2025
BREAKING: BLM activist Monica Cannon-Grant pleads guilty to 27 fraud charges, misusing over $1M from Violence in Boston for personal gain. Echoes Sir Maejor Page’s $450K scam conviction. A wake-up call for nonprofit accountability. pic.twitter.com/N9vvD369gB
— (@pr0ud_americans) September 14, 2025
Here’s a local video report:
She should pay back every penny.
The post Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle appeared first on The Gateway Pundit.
Politics
Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO)

As the Gateway Pundit reported yesterday, former MSNBC host and generally unhinged leftist Keith Olbermann, appeared to threaten CNN’s conservative pundit Scott Jennings on Twitter saying, ‘You’re next motherf**ker.’
Well, Olbermann may have gotten a phone call or a visit from the FBI because today he walked back those comments with a full-throated apology.
RedState has an update:
To quickly recap, Scott Jennings, a Salem Media Network radio host and conservative CNN political commentator, reacted to breaking news on Monday that Kimmel had been reinstated by tweeting, “So basically his employer suspended him for being an insensitive pr**k, and we don’t live in an authoritarian regime? Got it.”
This enraged Olbermann, who proceeded to tweet what many, including Jennings, perceived to be a threat. “You’re next, motherf**ker. But keep mugging to the camera.” Jennings tagged Patel and included a screengrab of the tweets in response.
Though the FBI hasn’t commented as to whether an investigation was launched, Olbermann ostensibly appears to have thought twice about what he tweeted and deleted, apologizing profusely in tweets posted on Tuesday and claiming what he wrote was “misinterpreted”:
See Olbermann’s tweet below:
I apologize without reservation to @ScottJenningsKY
Yesterday I wrote and immediately deleted 2 responses to him about Kimmel because they could be misinterpreted as a threat to anything besides his career. I immediately replaced them with ones specifying what I actually meant. pic.twitter.com/SPWLb73nEk
— Keith Olbermann (@KeithOlbermann) September 23, 2025
I oppose and condemn political violence, and the threat of it. All times are the wrong time to leave even an inadvertent impression of it – but this time is especially wrong
I should've acknowledged the deletion and apologized yesterday. I'm sorry I delayed.
— Keith Olbermann (@KeithOlbermann) September 23, 2025
Scott Jennings, always a class act, offered this hilarious response:
SCOTT JENNINGS: “Marking myself SAFE from that NUT, Keith Olbermann!” pic.twitter.com/EYZX6vm5Oh
— Dustin Grage (@GrageDustin) September 23, 2025
Keith Olbermann really needs help. The guy is just so out of control.
The post Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO) appeared first on The Gateway Pundit.
Politics
Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished

 Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson lived with his transgender partner – a male-to-female trans named Lance “Luna” Twiggs.
The FBI used Robinson’s texts with his transgender partner to solidify that Robinson was the assassin. Lance Twiggs has not been charged with any crime; however, federal authorities are still investigating.
Last week, Utah authorities released the text exchange between Tyler Robinson and his transgender lover, Lance Twiggs, sent shortly after Kirk’s assassination.
Utah County District Attorney Jeff Gray announced seven charges against Charlie Kirk assassin Tyler Robinson. They will also be seeking the death penalty.
Robinson was charged with:
– Count 1: Aggravated murder (capital offense)
– Count 2: Felony reckless discharge of a firearm causing bodily injury
– Count 3: Felony obstruction of justice for hiding the firearm
– Count 4: Felony obstruction of justice for discarding the clothing he wore during the shooting
– Count 5: Witness tampering for asking roommate to delete incriminating messages
– Count 6: Witness temperating for demanding trans roommate stay silent, and not speak to police
– Count 7: Commission of a violent offense in the presence of a child
Jeff Gray released the chilling texts between Tyler Robinson and his “love” Lance Twiggs.
Read the text exchange here:
 Tyler Robinson texts with transgender lover Lance Twiggs / 1
Tyler Robinson texts with transgender lover Lance Twiggs / 1
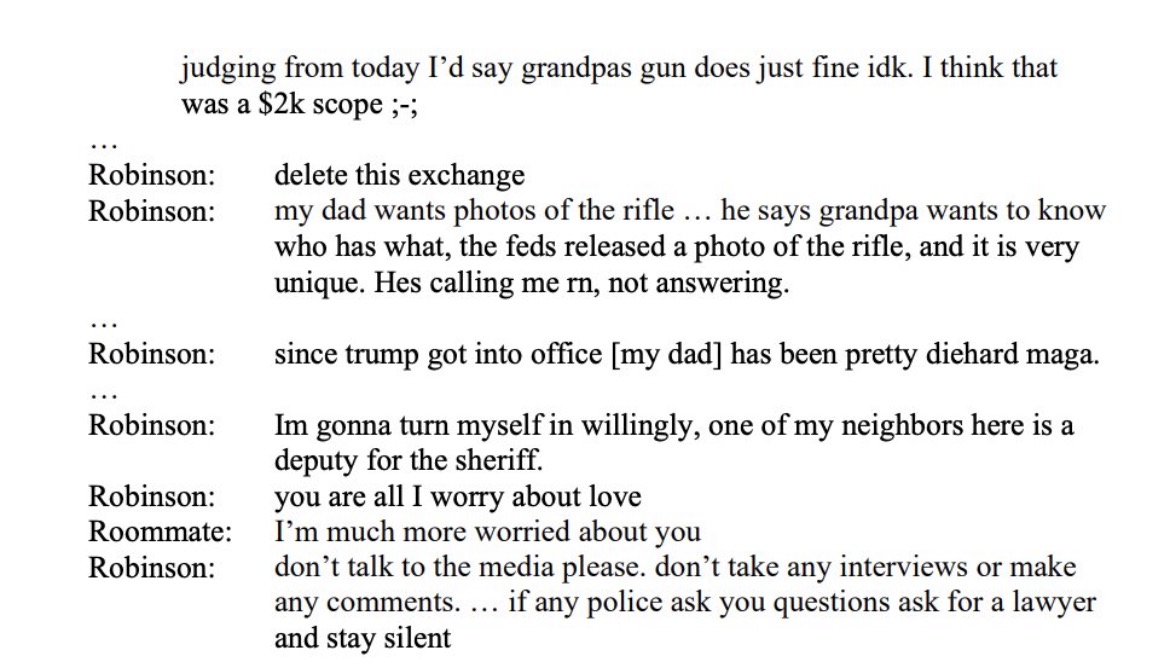 Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Lance Twiggs was reportedly cooperating with the FBI, however, according to the Daily Mail he has seemingly vanished.
“If [Lance Twiggs] ever comes back, it will be in a body bag,” a neighbor said to the Daily Mail. “That’s not a threat – I’m just saying that there are so many people who want a piece of him he’d be mad to show his face in public again. This was a generational event.”
The Daily Mail reported:
The Trans boyfriend of Charlie Kirk’s alleged assassin has fled their former lovenest – and locals tell the Daily Mail they never want to see him again.
Lance Twiggs, 22, was led away for questioning when police swooped on the smart three-bed condo he shared with accused gunman Tyler Robinson, 22.
Shaken neighbors say the part time plumber has not been back to the $320,000 property in St. George, Utah – one declaring: ‘Good riddance. I never want to see either of them again.’
His beaten-up Infinity compact is still parked in his space with his work gear tossed across the back seat and a sandwich wrapper and a drink on the front passenger seat.
Upstairs lights have been left on for more than a week and notes and Amazon packages are piling up outside the home owned by Twiggs’s devout Mormon family.
The post Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished appeared first on The Gateway Pundit.
-
 Entertainment6 months ago
Entertainment6 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment3 months ago
Entertainment3 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech6 months ago
The best sexting apps in 2025
-
 Entertainment5 months ago
Entertainment5 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech7 months ago
Tech7 months agoEvery potential TikTok buyer we know about
-
Tech7 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech7 months ago
Tech7 months agoAre You an RSSMasher?
-

 Politics7 months ago
Politics7 months agoDOGE-ing toward the best Department of Defense ever



