| What: | The creation of U.S. Cyber Command |
| When: | CYBERCOM was created as a sub-unified command in 2009, but its origins can be traced back to the 1980s. |
| Why it matters: | CYBERCOM is in charge of protecting DoD’s information systems and supporting the nation’s efforts to defend critical infrastructure from major cyber threats — its creation allowed the Defense Department to unify cyber operations and strengthen its cyber capabilities. |
Politics
Cyber Command adapts to realities of constant digital conflict


The story of U.S. Cyber Command doesn’t start in 2009 when it was formally established as a sub–unified command in 2009. The story really starts in the late 1980s when the first documented cases of cyber-espionage occurred during the early days of the internet.
In 1986, a systems administrator at the Lawrence Berkeley National Laboratory named Clifford Stoll uncovered a Soviet-backed hacking campaign targeting U.S military and research networks — a case he famously documented in The Cuckoo’s Egg. Two years later, the Morris Worm swept through the internet, but it wasn’t until the late 1990s that the Defense Department began to reckon with the strategic implications of the emerging threat environment.
In 1997, the Joint Chiefs of Staff ran an exercise called Eligible Receiver 97, in which NSA red team hackers demonstrated they could easily disrupt military systems and civilian infrastructure. Months later, the DoD created the Joint Task Force–Computer Network Defense (JTF-CND), laying the groundwork for what would eventually result in the establishment of Cyber Command a decade later.
“We’ve been grappling with the insecurity of cyberspace since we’ve been leveraging cyberspace, but we got to a point in the late 2000s where we recognized that the operational reality was sort of constant, or what we call persistent engagement now,” Richard Harknett, director of the center for cyber strategy and policy at the University of Cincinnati, told Federal News Network. “There was also this sort of perceptual reality that emerged, which was, ‘Oh, you could do big things in cyber.’ What happens if we mess around with electric grids and big critical infrastructure? So there was this operational reality, which was more about day-to-day exploitation. And then there was this perception of the reality that something really bad could happen and we need to get ourselves organized for this.”
The early days of Cyber Command were shaped by the perception that a massive, devastating digital attack could occur.
The natural inclination early on was to think about cyberspace and cyber deterrence just like the U.S. thought about the nuclear strategic environment and nuclear deterrence.
“We were thinking about it in a war context and so there was this default to how do we deal with war? We try to deter it,” Harknett said.
This perception was reinforced by the organizational structure of Cyber Command, which was placed under U.S. Strategic Command, the country’s nuclear command. So much of the early thinking about cyber operations revolved around how to deter war, rather than how to operate effectively in a constantly contested digital environment. But the threat wasn’t a “Cyber Pearl Harbor” as much as a persistent campaign of probing and exploiting networks across the federal government, defense industrial base, and critical infrastructure.
“We had a gap early on between the strategic view of cyber and the operational reality that Cyber Command and its capabilities were having to deal with,” Harknett said. “We have to actually, in my view, stop talking about cyber offense, cyber defense, and talk about cyber operations and cyber campaigns. They have both effects. They can have defensive effects, they can have offensive effects.”
The shift came with the “defend forward” and “persistent engagement” concepts, which were publicly announced in 2018 as part of a broader shift in U.S. cyber strategy. That meant moving Cyber Command from a reactive force right to a persistent force.
“To be persistent is to be, as [Gen. Paul Nakasone] noted, not reactive. It is about being proactive, but being proactive is not ipso facto offense. You don’t have to disrupt and destroy in order to set and reset this cyber architecture in a way that favors you and disfavors your opponents. That’s the whole notion of cyber campaigning. This is the cyber part of the fight, that you’re in continuous motion, and you’re going to move laterally, you’re going to move back and forward. It’s a better way of thinking about this space than this legacy, ‘Let’s go on the offense,’” Harknett said.
Recognizing that cyberspace had become vital to national security, Cyber Command was elevated to a unified combatant command in 2018. Between 2018 and 2020 the command received expanded presidential authorities to allow it to operate more proactively and persistently in cyberspace.
But having the legal authority to act and fully using those authorities are not the same, Harknett said. The Biden administration embraced the “defend forward” and “persistent engagement” notions, sometimes referring to them as “disruption campaigns.” Still, an open question remains around how rigorously these strategies have been implemented, how many bureaucratic or legal hurdles remain in place, and whether the operational tempo matches the intent behind the strategy.
One sign of progress is the increasing regularization of “hunt forward” operations, where Cyber Command deploys teams to allied nations to detect, expose and disrupt adversary malware on partner networks.
“We’re early in this and only a few years operating under authorities that are less reactive and more proactive. I think it’s a matter of understanding that we’re evolving to the space, in part my own view is that we’re catching up to some of our cyber adversaries who have been operating in this manner a lot longer than we have. I think the trend line is that operational reality and that strict perception of the strategy — that gap is closing. We’re starting to understand why our adversaries are below the threshold of armed conflict is because they can strategically gain in that space,” Harknett said.
Cyber Command 2.0
With the strategy in place, the command now needs to align its organizational structure, capabilities and partnerships to that “constant fight.”
“Cyber, you just can’t quit. You don’t have any time. You don’t have any day that you can take off. And so we have legacy organizational artifacts that need to evolve. That’s partly the relationships with the services. It’s partly in terms of how you develop capabilities, and how you fund,” Harknett said.
That’s what is expected to come from an extensive examination dubbed “Cyber Command 2.0” — the review is meant to address the command’s longstanding readiness and personnel challenges.
For now, the initiative’s four main efforts include a new force generation model for how each service provides cyber forces to CYBERCOM, an advanced training and education center to ensure forces have the training needed when arriving to their units, a talent management model, and a cyber innovation warfare center.
Separate Cyber Force?
Meanwhile, the debate over establishing a separate Cyber Force continues — the fiscal 2025 defense bill requires the Defense Department conduct an “evaluation of alternative organizational models for the cyber forces of the Armed Forces.” The bill, however, does not include a due date for the study.
Pentagon leaders have largely rejected the idea of a separate cyber branch, but proponents of the idea argue that fixing the nation’s cyber force generation system “demands nothing less than the establishment of an independent cyber service.”
“The inefficient division of labor between the Army, Navy, Air Force, and Marine Corps prevents the generation of a cyber force ready to carry out its mission. Recruitment suffers because cyber operations are not a top priority for any of the services, and incentives for new recruits vary wildly. The services do not coordinate to ensure that trainees acquire a consistent set of skills or that their skills correspond to the roles they will ultimately fulfill at CYBERCOM,” the Foundation for Defense of Democracies report report reads.
“Resolving these issues requires the creation of a new independent armed service — a U.S. Cyber Force — alongside the Army, Navy, Air Force, Marine Corps, and Space Force,” Mark Montgomery, a retired Navy rear admiral, and Erica Lonergan, an assistant professor at Columbia University, said in the report.
The post Cyber Command adapts to realities of constant digital conflict first appeared on Federal News Network.
Politics
Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle

Screencap of YouTube video.
A Black Lives Matter activist in Boston named Monica Cannon-Grant pleaded guilty to federal charges this week, admitting that she scammed donors and used their money to fund her own lavish lifestyle.
Cannon-Grant was previously held up as an admired figure. The city of Boston named her the Bostonian of the year at one point for her ‘social justice activism’ and she was even recognized by the Boston Celtics basketball team for her efforts.
She is now facing a minimum of two years in prison.
The New York Post reports:
BLM-linked activist admits conning donors to fund her lavish lifestyle
A once-celebrated Boston social activist has pleaded guilty to defrauding donors — including Black Lives Matter — out of thousands of dollars that she used as a personal piggy bank.
Monica Cannon-Grant, 44, pleaded guilty Monday to 18 counts of fraud-related crimes that she committed with her late husband while operating their Violence in Boston (VIB) activists group, according to the US Attorney’s Office in Massachusetts.
The activist scammed money — including $3,000 from a BLM group — while claiming it was to help feed children and run protests like one in 2020 over the murder of George Floyd and police violence.
Cannon-Grant also conned her way into getting $100,000 in federal pandemic-related unemployment benefits — which she used to pay off her personal auto loan and car insurance policy.
But she has now confessed to transferring funds to personal bank accounts to pay for rent, shopping sprees, delivery meals, visits to a nail salon — and even a summer vacation to Maryland.
Just amazing.
Monica Cannon-Grant stole from donors, scammed the government, and lived it up while preaching about oppression. BLM grift is the only nonprofit where fraud is part of the mission statement. https://t.co/ir3q9lqYrh
— Matthew Newgarden (@a_newgarden) September 23, 2025
BREAKING: BLM activist Monica Cannon-Grant pleads guilty to 27 fraud charges, misusing over $1M from Violence in Boston for personal gain. Echoes Sir Maejor Page’s $450K scam conviction. A wake-up call for nonprofit accountability. pic.twitter.com/N9vvD369gB
— (@pr0ud_americans) September 14, 2025
Here’s a local video report:
She should pay back every penny.
The post Black Lives Matter Activist in Boston Pleads Guilty to Federal Fraud Charges – Scammed Donors to Fund Her Lifestyle appeared first on The Gateway Pundit.
Politics
Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO)

As the Gateway Pundit reported yesterday, former MSNBC host and generally unhinged leftist Keith Olbermann, appeared to threaten CNN’s conservative pundit Scott Jennings on Twitter saying, ‘You’re next motherf**ker.’
Well, Olbermann may have gotten a phone call or a visit from the FBI because today he walked back those comments with a full-throated apology.
RedState has an update:
To quickly recap, Scott Jennings, a Salem Media Network radio host and conservative CNN political commentator, reacted to breaking news on Monday that Kimmel had been reinstated by tweeting, “So basically his employer suspended him for being an insensitive pr**k, and we don’t live in an authoritarian regime? Got it.”
This enraged Olbermann, who proceeded to tweet what many, including Jennings, perceived to be a threat. “You’re next, motherf**ker. But keep mugging to the camera.” Jennings tagged Patel and included a screengrab of the tweets in response.
Though the FBI hasn’t commented as to whether an investigation was launched, Olbermann ostensibly appears to have thought twice about what he tweeted and deleted, apologizing profusely in tweets posted on Tuesday and claiming what he wrote was “misinterpreted”:
See Olbermann’s tweet below:
I apologize without reservation to @ScottJenningsKY
Yesterday I wrote and immediately deleted 2 responses to him about Kimmel because they could be misinterpreted as a threat to anything besides his career. I immediately replaced them with ones specifying what I actually meant. pic.twitter.com/SPWLb73nEk
— Keith Olbermann (@KeithOlbermann) September 23, 2025
I oppose and condemn political violence, and the threat of it. All times are the wrong time to leave even an inadvertent impression of it – but this time is especially wrong
I should've acknowledged the deletion and apologized yesterday. I'm sorry I delayed.
— Keith Olbermann (@KeithOlbermann) September 23, 2025
Scott Jennings, always a class act, offered this hilarious response:
SCOTT JENNINGS: “Marking myself SAFE from that NUT, Keith Olbermann!” pic.twitter.com/EYZX6vm5Oh
— Dustin Grage (@GrageDustin) September 23, 2025
Keith Olbermann really needs help. The guy is just so out of control.
The post Keith Olbermann Backpedals Furiously With Apology for Threatening CNN’s Scott Jennings – Jennings Responds (VIDEO) appeared first on The Gateway Pundit.
Politics
Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished

 Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson and roommate Lance Twiggs
Charlie Kirk assassin Tyler Robinson lived with his transgender partner – a male-to-female trans named Lance “Luna” Twiggs.
The FBI used Robinson’s texts with his transgender partner to solidify that Robinson was the assassin. Lance Twiggs has not been charged with any crime; however, federal authorities are still investigating.
Last week, Utah authorities released the text exchange between Tyler Robinson and his transgender lover, Lance Twiggs, sent shortly after Kirk’s assassination.
Utah County District Attorney Jeff Gray announced seven charges against Charlie Kirk assassin Tyler Robinson. They will also be seeking the death penalty.
Robinson was charged with:
– Count 1: Aggravated murder (capital offense)
– Count 2: Felony reckless discharge of a firearm causing bodily injury
– Count 3: Felony obstruction of justice for hiding the firearm
– Count 4: Felony obstruction of justice for discarding the clothing he wore during the shooting
– Count 5: Witness tampering for asking roommate to delete incriminating messages
– Count 6: Witness temperating for demanding trans roommate stay silent, and not speak to police
– Count 7: Commission of a violent offense in the presence of a child
Jeff Gray released the chilling texts between Tyler Robinson and his “love” Lance Twiggs.
Read the text exchange here:
 Tyler Robinson texts with transgender lover Lance Twiggs / 1
Tyler Robinson texts with transgender lover Lance Twiggs / 1
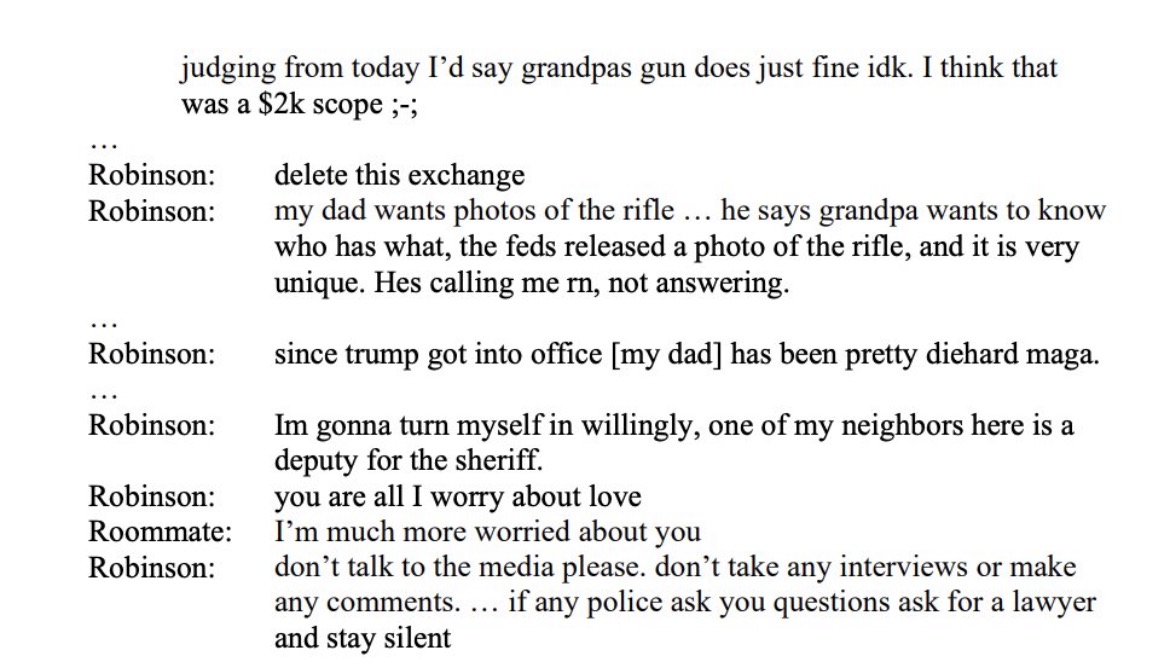 Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Kirk assassin Tyler Robinson texts with transgender lover Lance Twiggs / 2
Lance Twiggs was reportedly cooperating with the FBI, however, according to the Daily Mail he has seemingly vanished.
“If [Lance Twiggs] ever comes back, it will be in a body bag,” a neighbor said to the Daily Mail. “That’s not a threat – I’m just saying that there are so many people who want a piece of him he’d be mad to show his face in public again. This was a generational event.”
The Daily Mail reported:
The Trans boyfriend of Charlie Kirk’s alleged assassin has fled their former lovenest – and locals tell the Daily Mail they never want to see him again.
Lance Twiggs, 22, was led away for questioning when police swooped on the smart three-bed condo he shared with accused gunman Tyler Robinson, 22.
Shaken neighbors say the part time plumber has not been back to the $320,000 property in St. George, Utah – one declaring: ‘Good riddance. I never want to see either of them again.’
His beaten-up Infinity compact is still parked in his space with his work gear tossed across the back seat and a sandwich wrapper and a drink on the front passenger seat.
Upstairs lights have been left on for more than a week and notes and Amazon packages are piling up outside the home owned by Twiggs’s devout Mormon family.
The post Where is Lance Twiggs? Kirk Assassin’s Transgender Lover Has Vanished appeared first on The Gateway Pundit.
-
 Entertainment6 months ago
Entertainment6 months agoNew Kid and Family Movies in 2025: Calendar of Release Dates (Updating)
-

 Entertainment3 months ago
Entertainment3 months agoBrooklyn Mirage Has Been Quietly Co-Managed by Hedge Fund Manager Axar Capital Amid Reopening Drama
-
Tech6 months ago
The best sexting apps in 2025
-
 Entertainment5 months ago
Entertainment5 months agoKid and Family TV Shows in 2025: New Series & Season Premiere Dates (Updating)
-

 Tech7 months ago
Tech7 months agoEvery potential TikTok buyer we know about
-
Tech7 months ago
iOS 18.4 developer beta released — heres what you can expect
-

 Tech7 months ago
Tech7 months agoAre You an RSSMasher?
-

 Politics7 months ago
Politics7 months agoDOGE-ing toward the best Department of Defense ever



